How to Set Up Cron Jobs for Security Monitoring?
Security monitoring is a crucial part of protecting your system from potential threats. One way to ensure the security of your server is to use cron jobs for regular monitoring.
Cron is a standard tool for automating tasks in UNIX-like operating systems. It allows you to schedule the execution of specific commands and scripts. In this article, we will look at how to set up cron jobs for security monitoring.
Step 1: Creating a Monitoring Script
The first step in setting up a cron job for security monitoring is to create a script that will perform the necessary actions. In this script, you can use various utilities and commands to check the security status of the system.
For example, you can create a script using the chkrootkit command, which will check the system for rootkits, or use clamscan to scan the system for malware.
Step 2: Adding a Task to Cron
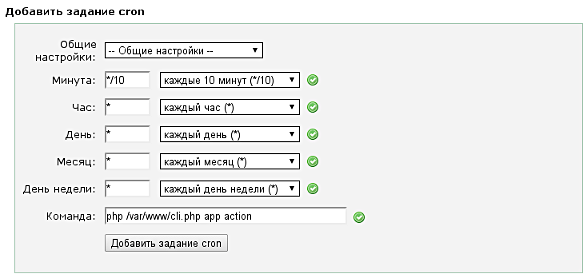
After creating the monitoring script, you need to add a task to cron. To do this, run the command crontab -e to edit the cron table. Enter a line in the following format:
* * * * * /path_to_script/script.sh
This means that the task will be executed every minute. You can configure the task execution schedule by changing the time values in the line. For example, the line 30 * * * * /path_to_script/script.sh means that the task will be executed every hour at 30 minutes.
Step 3: Checking Task Execution
After adding the task to cron, you need to make sure that it is executed correctly. To do this, you can view the task execution logs using the command grep cron /var/log/syslog.
If the task is executed successfully, you will see the corresponding entries in the logs. In case of problems, view the logs to identify possible errors.
Conclusion
Setting up cron jobs for security monitoring can help you identify potential threats in a timely manner and ensure the security of your system. By following these steps, you can set up automated monitoring, which will make your system more secure.