How to Protect Server Encryption Keys?
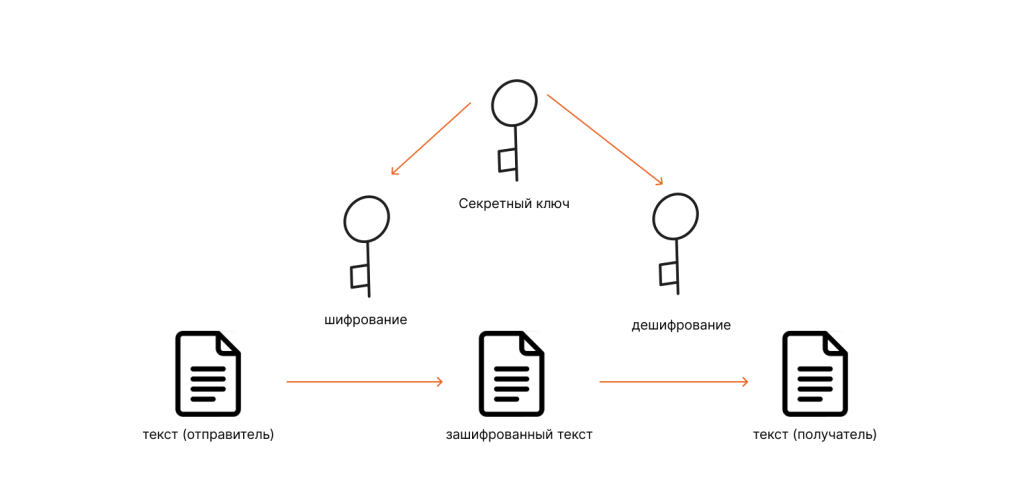
The security of server encryption keys is one of the key aspects of protecting information on the network. Key leakage can lead to serious consequences, including the leakage of confidential data and access to protected information. Therefore, it is extremely important to ensure reliable protection of encryption keys on servers.
In this article, we will look at the main ways to protect server encryption keys and recommendations for their use.
Use Strong Encryption Algorithms
One of the first steps to protecting server keys is to use strong encryption algorithms. It is necessary to choose algorithms that provide a high level of security and have a good reputation in the cryptography community.
Some of the most common and secure encryption algorithms include AES, RSA, and ECC. Make sure your server keys use these algorithms to protect your data.
Store Keys in a Secure Location
It is important to store server encryption keys in a secure location inaccessible to unauthorized access. The ideal option is to store keys in a separately protected storage, different from the server.
It is also recommended to regularly update and regenerate encryption keys to prevent possible leaks.
Limit Access to Keys
To ensure maximum protection of server keys, it is necessary to restrict access to them only to authorized persons. Set strict access rules and identity verification for those who have access to encryption keys.
This will help prevent possible threats from attackers who may try to gain access to the keys and use them for malicious purposes.
Use Multi-Factor Authentication
To enhance the security of server keys, it is recommended to use multi-factor authentication when accessing them. This will further protect the keys and reduce the risk of their compromise.
Make sure that access to encryption keys requires not only a password or PIN code, but also additional authentication factors, such as biometric data or one-time codes.
Regularly Check Key Security
To detect possible vulnerabilities and key leaks, it is necessary to regularly conduct security checks and audits. This will allow you to identify problems in a timely manner and prevent threats to server keys.
Use specialized tools and services to monitor the security of encryption keys and respond to any suspicious activity or vulnerabilities detected.
Conclusion
Protecting server encryption keys plays an important role in ensuring the security of your information. Follow the recommendations for protecting keys, use strong encryption algorithms, store keys in a secure location, and restrict access to them only to authorized persons.
Following these principles will help protect your data from leaks and hacker attacks, providing reliable protection of server encryption keys.