How to Restrict SSH Access to Only One IP?
SSH (Secure Shell) is one of the most common ways to remotely manage a server. However, to ensure server security, it’s sometimes necessary to restrict SSH access to only specific servers with IP addresseses. In this article, we’ll explore how to deny SSH access to everyone except one particular IP address.First, you need to ensure that you have access to the server and administrator privileges. Next, connect to the server via SSH and enter the console.
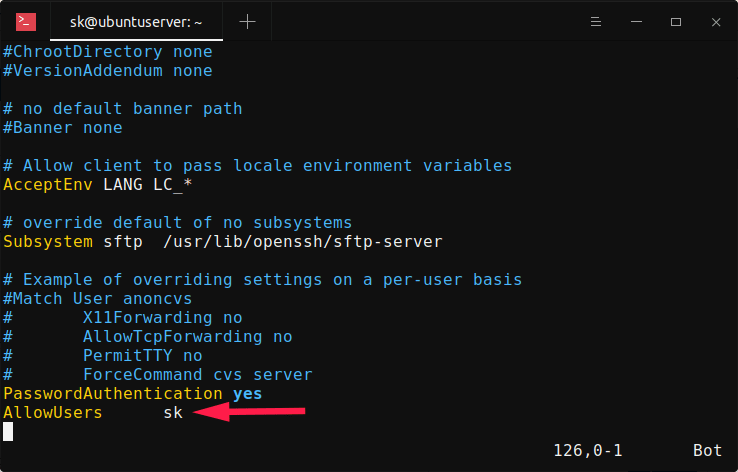
To deny SSH access to everyone except one IP address, you’ll need to edit the firewall settings. The most popular firewall for Linux servers is iptables.
Here’s the command you can use to allow SSH access only for one specific IP address (in this case, 192.168.1.100):
iptables -A INPUT -p tcp --dport 22 -s 192.168.1.100 -j ACCEPT
iptables -A INPUT -p tcp --dport 22 -j DROPWith these commands, you’ll allow SSH access only for the IP address 192.168.1.100, and all other IPs will be blocked. Don’t forget to replace 192.168.1.100 with the actual IP address you’ll be connecting to the server from.
After you’ve made changes to the firewall settings, you need to apply them:
iptables-save > /etc/iptables/rules.v4Now all changes are saved, and SSH access is restricted to only the specified IP address. Remember that when working with the firewall, it’s always recommended to be careful to avoid blocking your own access to the server. Check the firewall settings before applying them to make sure you haven’t locked yourself out.
We hope this article was helpful to you. Be vigilant and monitor the security of your server!
«`