How to Restrict Sudo Access?
sudo is a utility for executing commands as another user. It’s very convenient, but it’s essential to ensure system security so unauthorized individuals can’t gain sudo access and mess up something important. Let’s explore several ways to restrict sudo access.
Using the /etc/sudoers File
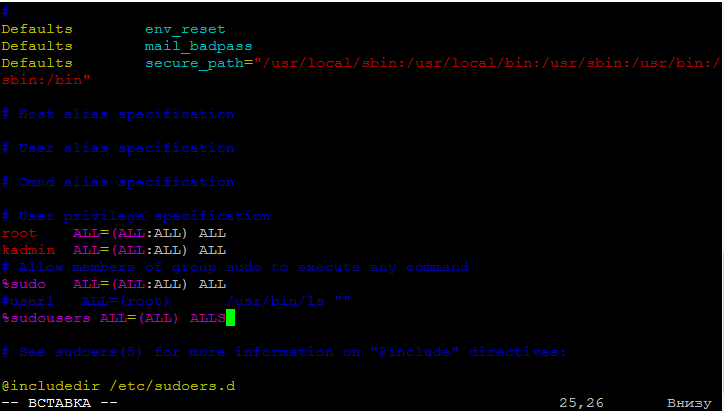
One of the most common and straightforward ways to restrict sudo access is by using the /etc/sudoers file. In this file, you can specify who can execute which commands using sudo.
To edit the /etc/sudoers file, use the visudo command. This command ensures correct handling of the file to avoid errors.
Example of adding the user «user» to sudo:
user ALL=(ALL:ALL) ALL
Where:
- user – the username
- ALL – the host from which the user can use sudo
- ALL – the user on whose behalf sudo can be used
- ALL – the commands that the user can execute using sudo
Using Groups
Another way to restrict sudo access is by using groups. Create a new group and add only the users who need sudo access to it. Then, in the /etc/sudoers file, specify the group and the commands it can execute.
Example of adding the «sudo_users» group and allowing it to execute all commands:
%sudo_users ALL=(ALL:ALL) ALL
Using sudoers.d Policy
For more convenient and flexible configuration of sudo access, you can use the sudoers.d policy. In this case, each user or group will have their own file with access rights.
Create a new file in the /etc/sudoers.d directory, for example, user1, and specify which commands can be executed:
user1 ALL=(ALL:ALL) /bin/ls, /bin/cat
After creating the file, be sure to check it for errors using the command visudo -cf /etc/sudoers.d/user1.
Conclusion
Restricting sudo access is an important part of ensuring system security. Use the suggested methods to control who can execute what using sudo and prevent possible attacks or unintentional errors.
Remember that security is the foundation of stable operation of your system.