Colleagues, greetings! In our ever-changing digital landscape, where the demands for flexibility, control, and security are growing exponentially, choosing the right hosting platform is becoming a cornerstone for any serious project. Today, we will delve into detail one of the most balanced and sought-after solutions on the market – a VPS server. You may already have experience with VPS, but have you considered all its nuances, potential, and why in 2025 it remains not just relevant, but often an indispensable tool for developers, system administrators, and, of course, cybersecurity specialists? This article is not just a primer. It’s a deep dive into the world of what a VPS server is, its architecture, advantages, use cases, and, importantly for our audience, security aspects. We will try to explain what a VPS server is in simple terms, but without sacrificing technical depth. Get ready, there will be a lot of useful information, practical tips, and food for thought. Let’s go explore the virtual horizons!
Table of Contents
- What is a server in principle? A brief overview for completeness
- The Magic of Virtualization: How many virtual servers are created from one physical server
- Hypervisors: Conductors of the Virtual Orchestra
- What is a VPS server? Detailed definition and key characteristics
- Analogy: VPS as an apartment in a multi-apartment building
- VPS vs. Shared Hosting: What is the fundamental difference?
- VPS vs. Dedicated Server: Balancing price and capabilities
- What is a VPS server? Diving deeper
- Types of VPS by management level: Managed vs. Unmanaged
- VPS Virtualization Technologies: KVM, OpenVZ, Xen, Hyper-V – which to choose?
- KVM (Kernel-based Virtual Machine)
- OpenVZ (Open Virtuozzo)
- Xen
- Hyper-V
- Why a VPS server is needed in 2025? Use cases
- Hosting websites and web applications
- Development and testing environments (Dev/Test Environments)
- Hosting specific applications (game servers, CRM, ERP)
- Creating your own VPN server
- Deploying a mail server
- Server for backup and data storage
- VPS server in the arsenal of a cybersecurity specialist
- Penetration testing lab
- Isolated environment for malware analysis
- Deploying a Honeypot (hacker bait)
- Nodes for secure communications (Tor, I2P)
- Centralized log collection and analysis (ELK Stack, Splunk Free)
- Personal cloud storage (Nextcloud, OwnCloud)
- Advantages of using a VPS server
- Full control and customization flexibility (Root access)
- Resource scalability
- Guaranteed resources and performance
- Increased security and isolation
- Cost-effectiveness
- Disadvantages and points to consider when choosing a VPS server
- Technical knowledge requirements (especially for Unmanaged VPS)
- Responsibility for administration and security
- Resource limitations compared to Dedicated
- «Noisy neighbor» effect (less relevant for KVM)
- How to choose the right VPS provider and plan?
- Key parameters: CPU, RAM, disk (SSD/NVMe), traffic
- Geographic location of the data center
- Quality of technical support
- Uptime guarantees (SLA)
- Operating system selection
- Availability of DDoS protection
- Backup and snapshot capabilities
- Initial setup of a VPS server: Basic steps
- Connecting to VPS via SSH
- System update
- Creating a new user and configuring sudo
- Basic firewall configuration (UFW/firewalld)
- VPS server security: Practical recommendations for the paranoid (and not only)
- Strengthening SSH access (keys, disabling root, changing the port)
- Configuring Fail2Ban to protect against brute-force attacks
- Using intrusion detection/prevention systems (IDS/IPS)
- Regular security audits and vulnerability scanning
- Disabling unnecessary services and strengthening running ones
- Monitoring and logging
- VPS server vs. Cloud platforms (IaaS): Which to choose?
- The future of VPS: Trends for 2025 and beyond
- A relevant quote
- Conclusions
What is a server in principle? A brief overview for completeness
Before we delve into the specifics of what a VPS server is, let’s quickly refresh our memory on what a server is in its classical understanding. A server is, essentially, a powerful computer (or software running on it) that provides specific services or resources to other computers (clients) on a network. This could be a web server that delivers web pages to your browser, a file server for storing shared documents, a mail server for processing email, a game server for multiplayer games, and so on.
A physical server (dedicated server) is a separate machine entirely dedicated to the needs of a single client. It possesses all the resources of this machine: processor (CPU), random access memory (RAM), disk space (HDD/SSD), and network channel. This provides maximum performance and control, but it is also correspondingly expensive and requires considerable administrative effort.

The Magic of Virtualization: How many virtual servers are created from one physical server
The key technology underlying the VPS server is virtualization. Virtualization allows you to create multiple isolated virtual machines (VMs) on a single physical server. Each such VM behaves like a full-fledged, independent server with its own operating system, allocated (or guaranteed) resources (part of the CPU, RAM, disk), and full root access.
Hypervisors: Conductors of the Virtual Orchestra
Special software – a hypervisor (or virtual machine monitor, VMM) – is responsible for creating and managing virtual machines. The hypervisor is installed either directly on «bare metal» (Type 1, bare-metal, such as VMware ESXi, KVM, Xen, Microsoft Hyper-V), or on top of the host’s main operating system (Type 2, hosted, such as VMware Workstation, Oracle VirtualBox, Parallels Desktop). For VPS server hosting, Type 1 hypervisors are usually used, as they provide better performance and isolation.
The hypervisor distributes the resources of the physical server among virtual machines, ensures their isolation, and manages their lifecycle. Thanks to it, problems or actions in one VM (e.g., reboot, software installation, even a critical error) do not affect other VMs running on the same physical host.
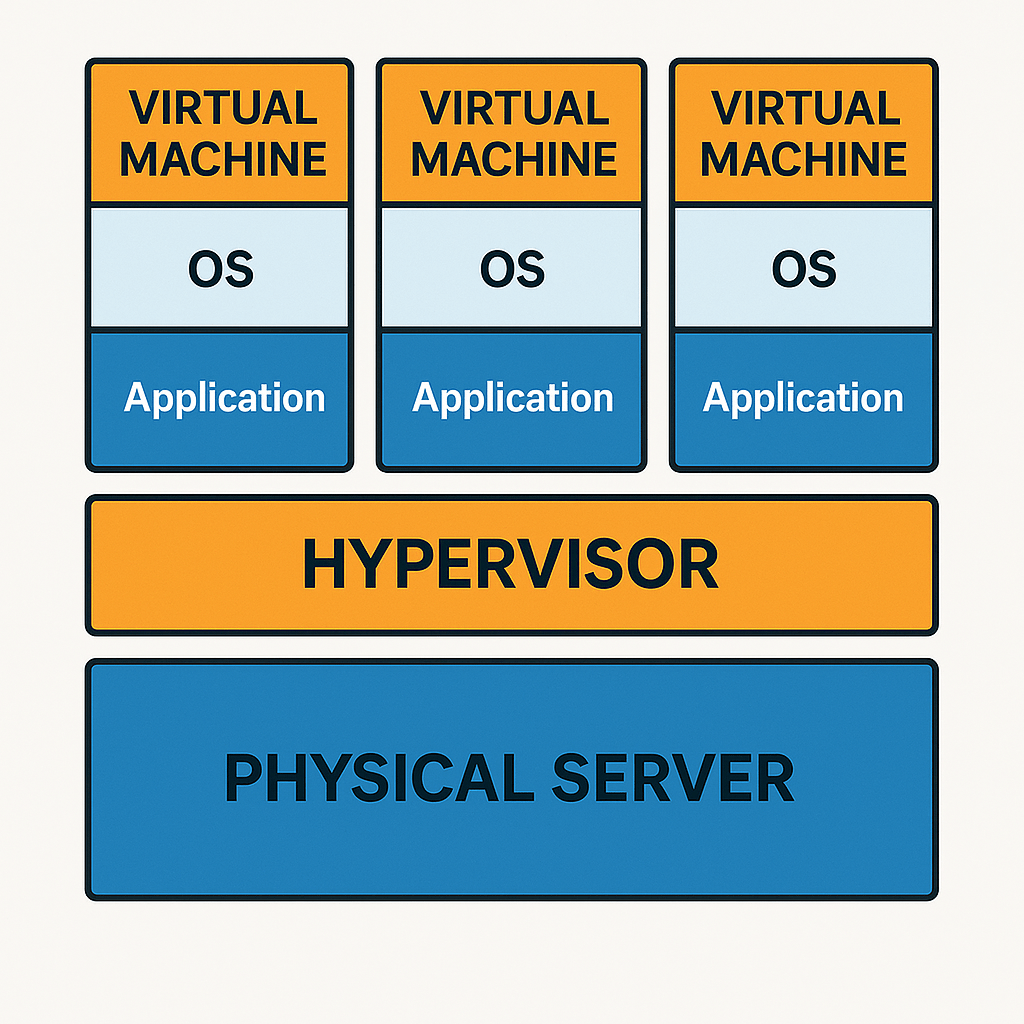
What is a VPS server? Detailed definition and key characteristics
So, a VPS server (Virtual Private Server) is a hosting service where the user is provided with a virtual machine with a guaranteed set of resources and full access to the operating system (root access in Linux, Administrator in Windows). In essence, it is an emulation of a separate physical server based on a more powerful physical server shared among several users.
Key characteristics of a VPS server:
- Isolation: Each VPS runs in its own isolated environment. Processes, files, and users of one VPS are invisible to other VPSs on the same physical server.
- Guaranteed resources: The user receives a certain amount of processor time (vCPU), random access memory (RAM), and disk space. These resources are usually guaranteed and are not shared with «neighbors» as happens on shared hosting (although the nuances depend on the type of virtualization and the provider’s policy).
- Root access/Administrator: The user has full administrative access to their virtual machine. This allows them to install any software, configure the operating system, modify configuration files, manage services, etc.
- Dedicated IP address: Each VPS is usually assigned at least one static IP address.
- OS selection: The user can choose the operating system for their VPS from the list offered by the provider (various Linux distributions, Windows Server) or even install their own from an ISO image (if the provider allows it).
Analogy: VPS as an apartment in a multi-apartment building
To better understand what a VPS server is, imagine a multi-apartment building.
- Dedicated Server – is a separate private house. All resources (land, utilities) belong to you. Maximum freedom, but also maximum costs and responsibility.
- Shared Hosting – is a room in a dormitory. You have your own bunk, but the kitchen, bathroom, and other amenities are shared. If your neighbors are noisy or cook a lot (consume resources), it will affect you. Control is minimal.
- VPS server – is a separate apartment in this building. You have your own walls, your own kitchen, your own bathroom (guaranteed resources). You can do renovations, arrange furniture as you wish (install software, configure the OS). You are isolated from your neighbors, although the building (physical server) is shared. This is the golden mean in terms of price, control, and resources.
VPS vs. Shared Hosting: What is the fundamental difference?
| Parameter | Shared Hosting | VPS server |
|---|---|---|
| Isolation | Low (resources and IP are often shared, problems with one client can affect others) | High (each VPS is isolated, has its own resources and IP) |
| Resources (CPU, RAM) | Shared, not guaranteed (can «float») | Guaranteed (or with high priority) |
| Root access/Admin. rights | No | Yes |
| Software installation | Only from the provider’s offered list | Any software compatible with the OS |
| OS configuration | Impossible | Full freedom of configuration |
| Dedicated IP address | Usually no (shared IP, allocated for an extra fee) | Yes, usually one or more |
| Level of control | Minimal | High |
| Technical knowledge | Minimal | Required (especially for Unmanaged) |
| Price | Low | Medium |
For a cybersecurity specialist, Shared Hosting is practically unacceptable due to the lack of control, the shared environment, and potential risks from «neighbors». A VPS server, however, provides the necessary level of isolation and control for many tasks.
VPS vs. Dedicated Server: Balancing price and capabilities
| Parameter | VPS server | Dedicated Server |
|---|---|---|
| Resources | Part of the physical server’s resources | All resources of the physical server |
| Performance | Good, but limited by the allocated quota | Maximum, limited only by the «hardware» |
| Scalability | Easily scalable (within the physical host) | Difficult to scale (requires hardware replacement or migration) |
| Price | Medium | High |
| Hardware management | No (maintained by the provider) | Full (if colocation) or partial (if rental) |
| Hardware customization | No (uses what the provider has) | Possible (choice of components) |
A VPS server offers a significant portion of the advantages of a dedicated server (control, root access, guaranteed resources) at a much lower price. For many tasks where the full power of a physical machine is not required, VPS is the optimal choice.
What is a VPS server? Diving deeper
Now that we understand the general concept, let’s consider some technical aspects of the VPS server in more detail.
Types of VPS by management level: Managed vs. Unmanaged
This is one of the key differences when choosing a VPS server:
- Unmanaged VPS: The provider is only responsible for the operation of the physical server and network, as well as the availability of your VPS as a virtual machine. All OS and software configuration, updates, security, backups, and software troubleshooting are entirely your responsibility.
- For whom: Experienced system administrators, developers, cybersecurity specialists who need full control and are ready to handle administration themselves. This is the most flexible and usually the cheapest option.
- Managed VPS: The provider takes on some or all of the administration tasks for your VPS server. The scope of services can vary: from basic configuration and control panel installation to full monitoring, updates, security, and software assistance.
- For whom: Users without deep technical knowledge in administration, companies that do not have a dedicated system administrator, or those who want to focus on their project rather than on the technical aspects of the server. Managed VPS is usually more expensive.
For most cybersecurity specialists who value control and want to independently configure the environment for their needs (e.g., for a penetration testing lab or malware analysis), an Unmanaged VPS will be preferable. However, if the VPS is used to host a critical service and there is little time for administration, a Managed VPS may be a good choice.
VPS Virtualization Technologies: KVM, OpenVZ, Xen, Hyper-V – which to choose?
The type of virtualization technology used by the provider directly affects the performance, isolation, available OS, and capabilities of the VPS server.
KVM (Kernel-based Virtual Machine)
KVM is a hardware virtualization technology for Linux based on the x86 architecture. KVM is part of the Linux kernel and uses it to manage memory and the scheduler, as well as emulates hardware for guest operating systems. Each KVM VPS is a full-fledged virtual machine with its own kernel, providing a high level of isolation and allowing you to run virtually any OS (Linux, Windows, *BSD).
- Advantages:
- Excellent resource isolation (memory, CPU).
- Ability to install any OS (including Windows).
- A separate kernel for each VPS (you can modify it, load your own modules).
- Good performance, close to «native».
- SWAP partition support.
- Disadvantages:
- May have slightly higher resource overhead (memory, disk) compared to container virtualization.
- Usually slightly more expensive than OpenVZ.
Recommendation: KVM is perhaps the most popular and recommended choice for most tasks, especially if stability, isolation, and the ability to run different operating systems are important. For cybersecurity, this is often the best option.
OpenVZ (Open Virtuozzo)
OpenVZ is a container virtualization technology (or operating system-level virtualization) for Linux only. All VPS containers on OpenVZ use a common modified kernel of the host machine. This provides lower overhead and higher VPS density on a single physical server, but has its limitations.
- Advantages:
- Low overhead, high performance for many tasks.
- Usually cheaper than KVM.
- Fast VPS creation and launch.
- Disadvantages:
- Only Linux distributions can be run.
- Shared kernel for all VPS – inability to modify the kernel, load your own modules (for example, for VPN protocols like WireGuard, if they are not included in the host kernel).
- Resource isolation may be less strict (risk of «overselling», when the provider sells more resources than actually available).
- Some applications may not work correctly due to containerization limitations (for example, Docker in Docker can be problematic).
- Often there is no full SWAP, vSWAP (burst RAM) is used, which is not always good.
Recommendation: OpenVZ may be suitable for simple websites or tasks that do not require specific kernel settings or Windows. For serious projects and cybersecurity tasks, it’s better to avoid if there is an alternative in the form of KVM.
Xen
Xen is a cross-platform type 1 hypervisor (bare-metal) that supports both paravirtualization (PV) and full hardware virtualization (HVM). HVM allows you to run any unmodified OS (including Windows), PV requires a modified guest OS kernel (mostly Linux) for better performance.
- Advantages:
- Mature and stable technology.
- Good performance, especially with PV.
- Support for a wide range of OS (with HVM).
- Used by major cloud providers (for example, Amazon AWS EC2 was based on Xen for a long time, now switching to KVM (Nitro)).
- Disadvantages:
- Can be more difficult to configure and manage compared to KVM.
- In recent years, KVM has gained greater popularity in the VPS hosting segment.
Recommendation: Xen is a reliable choice if the provider offers it and has a good reputation. In terms of capabilities, it is close to KVM.
Hyper-V
Hyper-V is a hardware virtualization technology from Microsoft, built into Windows Server and client versions of Windows. Allows you to run both Windows and Linux guest operating systems.
- Advantages:
- Excellent integration with the Microsoft ecosystem.
- Good performance for Windows guests.
- Support for Linux guests (via Linux Integration Services).
- Disadvantages:
- Most often used for Windows VPS, which is usually more expensive due to Windows Server licensing.
- Less popular for Linux VPS compared to KVM or Xen.
Recommendation: If you need a Windows VPS server, then Hyper-V will be a natural and good choice. For Linux tasks, KVM is more often chosen.

Why You Need a VPS Server in 2025? Use Cases
The flexibility and control provided by a VPS server open up a wide range of possibilities. In 2025, as performance and security requirements continue to grow, these scenarios become even more relevant.
Hosting Websites and Web Applications
This is perhaps the most common scenario. A VPS server is ideal for:
- High-traffic websites: Online stores, popular blogs, forums that have outgrown the capabilities of shared hosting.
- Multiple websites: You can host many of your projects on one VPS (within the allocated resources).
- Websites with special requirements: If you need specific PHP modules, non-standard web server configuration (Nginx, Apache), specific software versions that are not available on shared hosting.
- Web applications on Python (Django, Flask), Ruby (Rails), Node.js, Java: VPS gives you full control over the environment for running such applications.
Development and Testing Environments (Dev/Test Environments)
Developers love VPS servers for the ability to:
- Create isolated environments: For each project or even branch, you can set up a separate VPS configured identically to the production environment.
- Integrate with CI/CD: A VPS can serve as a platform for continuous integration and delivery systems (Jenkins, GitLab CI).
- Test software in various configurations: Easily deploy different versions of OS or software to check compatibility.
- Use snapshots: Many providers offer the ability to take «snapshots» of the VPS state, which is very convenient for reverting to a previous version in case of an unsuccessful experiment.
Hosting Specific Applications (Game Servers, CRM, ERP)
- Game servers: For games like Minecraft, Counter-Strike, Rust, and others, where low ping and stability are important, a VPS server with a good channel and sufficient RAM/CPU is an excellent choice.
- CRM/ERP systems: Small and medium-sized companies can deploy their customer relationship management or enterprise resource planning systems on a VPS.
- VoIP services: For example, Asterisk or FreePBX for organizing IP telephony.
- Bots for messengers, parsers, and other custom applications.
Creating Your Own VPN Server
In 2025, the issues of privacy and security of Internet connections are more relevant than ever. On a VPS server, you can easily deploy your own VPN server (OpenVPN, WireGuard, IPSec/L2TP). This provides:
- Full traffic control: You know for sure that your data is not logged and not transferred to third parties (unlike many public VPN services).
- Circumventing geo-restrictions: By choosing a VPS in the required country, you can access content that is geographically restricted.
- Secure connection to public Wi-Fi networks.
- Creating a secure channel between your devices or offices.
To install, for example, OpenVPN on Ubuntu/Debian, scripts such as openvpn-install by Nyr are often used, which automate the process.
wget https://git.io/vpn -O openvpn-install.sh
chmod +x openvpn-install.sh
sudo ./openvpn-install.shWireGuard is also gaining popularity due to its simplicity and performance. Many providers already offer kernels with WireGuard support on KVM VPS.
Deploying a Mail Server
Although this is a complex task that requires in-depth knowledge (configuring Postfix, Dovecot, SpamAssassin, DKIM, SPF, DMARC), your own mail server on a VPS server gives you full control over your email, eliminating restrictions and potential surveillance from mail providers. For simplification, you can use ready-made builds such as Mail-in-a-Box or Mailcow.
Server for Backup and Data Storage
A VPS server with large disk space can be used for:
- Remote backup of data from your workstations, other servers (for example, using rsync, Restic, BorgBackup).
- Creating a personal cloud storage (see below).
VPS Server in a Cybersecurity Specialist’s Arsenal
And here’s where it gets interesting for our audience. A VPS server is a real training ground and working tool for a cybersecurity specialist.
Penetration Testing Lab
On an Unmanaged KVM VPS, you can deploy a full-fledged penetration testing lab:
- Installing specialized OS: Kali Linux, Parrot OS, or BlackArch Linux (you can use ISO, if the provider allows, or install the necessary tools on a standard distribution).
- Scanning and reconnaissance: Run Nmap, Masscan, OSINT tools from an external IP address without «exposing» your home or corporate network. (Warning: only on authorized targets!).
- Hosting a C2 server (Command and Control): For legitimate Red Team operations and exercises.
- Testing exploits in an isolated environment.
Isolated Environment for Malware Analysis
VPS (especially with snapshot capabilities) is a great place to create a «sandbox» for dynamic and static malware analysis. You can safely run suspicious files without risking your main system. After analysis, the VPS can be reverted to a clean state or simply deleted.
Deploying a Honeypot (Bait for Hackers)
A VPS server is ideal for hosting honeypots (e.g., Cowrie, Dionaea, T-Pot) to collect information about attackers, their methods, and tools. This allows you to study current threats in the «wild».
Nodes for Secure Communications (Tor, I2P)
You can set up a Tor (relay or bridge) or I2P node on your VPS server, contributing to the development of these networks and increasing your own anonymity when using them (if it is your exit node).
Centralized Log Collection and Analysis (ELK Stack, Splunk Free)
A small VPS server can be used to aggregate logs from your various devices and systems with subsequent analysis using tools such as the ELK Stack (Elasticsearch, Logstash, Kibana) or the free version of Splunk. This helps in the timely detection of security incidents.
Personal Cloud Storage (Nextcloud, OwnCloud)
Using software like Nextcloud or OwnCloud on your VPS server, you can create an analog of Dropbox or Google Drive, but with full control over your data. File synchronization, calendars, contacts, online document editors – all under your control.
Advantages of Using a VPS Server
Summing up the intermediate result, let’s highlight the main strengths of a VPS server.
Full Control and Flexibility of Configuration (Root Access)
This is the main advantage. You can install any OS (from available or your own ISO), any software, configure the kernel (on KVM/Xen), firewall, network services – everything you need for your project. For a cybersecurity specialist, this means the ability to create an environment that precisely matches the tasks.
Resource Scalability
If your project needs more resources (CPU, RAM, disk), most providers allow you to easily and quickly (often with minimal or no downtime) switch to a more powerful tariff plan. This is much easier than upgrading a physical server.
Guaranteed Resources and Performance
Unlike shared hosting, where resources are shared unpredictably, a VPS server (especially on KVM) provides you with a guaranteed minimum of CPU, RAM, and disk IOPS. This ensures stable and predictable performance.
Increased Security and Isolation
Thanks to virtualization, your VPS is isolated from «neighbors». Their actions, vulnerabilities, or even infection with malware (theoretically) should not affect your system. You can also configure your own firewall rules, IDS/IPS, and other security measures.
Cost-Effectiveness
A VPS server offers significantly more capabilities and control than shared hosting, at a very reasonable price. And it is significantly cheaper than renting a dedicated physical server, while providing a comparable level of control for many tasks.
Disadvantages and Points to Consider When Choosing a VPS Server
Despite all the advantages, a VPS server also has its own features that may be disadvantages for some users.
Technical Expertise Requirements (Especially for Unmanaged VPS)
If you choose an Unmanaged VPS, be prepared to administer Linux or Windows Server yourself: configure the web server, database, mail, ensure security, update software, and troubleshoot. This requires certain skills and time.
Responsibility for Administration and Security
With great power (root access) comes great responsibility. You are fully responsible for the security of your VPS. Incorrect configuration, untimely updates, weak passwords – all this can lead to hacking. The provider will not be responsible for this (on Unmanaged VPS).
Resource Limitations Compared to Dedicated
Although resources are guaranteed, they are still part of the common pool of the physical server. If you need maximum CPU performance, a huge amount of RAM, or super-fast disks for very high-load projects, then a dedicated server may be preferable. However, modern VPS servers on NVMe drives and powerful CPUs can often compete with budget «dedicated» servers.
The «Noisy Neighbor» Effect (Less Relevant for KVM)
Theoretically, if one of the VPSs on the same physical host creates an excessive load on shared components (for example, a network interface or disk subsystem, if there are no strict IOPS quotas), this may slightly affect the performance of your VPS. On KVM virtualization with strict resource quotas, this effect is minimized, but on OpenVZ or with unscrupulous providers, it may manifest itself.
How to Choose the Right VPS Provider and Tariff Plan?
Choosing a provider is a responsible step. Here’s what you should pay attention to when searching for your ideal VPS server:
Key Parameters: CPU, RAM, Disk (SSD/NVMe), Traffic
- CPU (vCPU): Number of virtual CPU cores and their clock speed. 1-2 vCPUs are sufficient for most websites. More are needed for more demanding applications or compilation tasks.
- RAM (Random Access Memory): One of the most important parameters. For a simple Linux server without graphics and a lightweight web server, 512MB-1GB might be enough. For websites on CMS, databases, and game servers – 2GB and above. Windows VPS requires a minimum of 2GB, comfortably – from 4GB.
- Disk:
- Type: Definitely choose SSD, and even better – NVMe SSD. They are significantly faster than traditional HDDs and substantially impact the overall server responsiveness. HDD VPS in 2025 is archaic, unless it’s for cold storage of backups.
- Capacity: Depends on your needs. The Linux OS occupies 5-10GB, Windows Server – 20-30GB. Plus space for your files, databases, and logs.
- Traffic/Bandwidth: Most providers offer either unlimited traffic at a certain speed (e.g., 100 Mbps), or a limited amount of traffic per month (e.g., 1-5 TB). Assess your needs. For most websites, 100 Mbps and 1-2 TB of traffic are more than enough.
Data Center Location
Choose a data center (DC) as close as possible to your target audience. This will reduce network latency (ping) and improve website loading speed/application response time. If your audience is in Europe, choose a DC in Germany, the Netherlands, or France. If in the CIS – accordingly. For global projects, you can use a CDN.
Technical Support Quality
Even if you get an Unmanaged VPS, you might sometimes need support (e.g., network issues on the provider’s side, VPS unavailability). Read reviews about the speed and quality of support response. 24/7 support is a big plus.
Uptime Guarantees (SLA)
Good providers guarantee uptime at 99.9% or higher (Service Level Agreement). Clarify what compensation is provided in case of SLA violation.
Operating System Selection
Make sure the provider offers the OS you need. Popular Linux distributions for VPS servers:
- Ubuntu Server: Download. Very popular, large community, lots of documentation. Good for beginners and experienced users.
- Debian: Download. Known for its stability and reliability. The choice of many «old-school» admins.
- CentOS Stream / AlmaLinux / Rocky Linux: CentOS Stream, AlmaLinux, Rocky Linux. Free RHEL alternatives. Popular in the enterprise environment, often used with control panels like cPanel.
- Windows Server: If you need specific Microsoft applications (ASP.NET, MSSQL). The license is usually included in the VPS cost and makes it more expensive than Linux alternatives.
The ability to install an OS from your own ISO image is a big plus for flexibility (especially for KVM VPS).
DDoS Protection
Basic DDoS protection (at the L3/L4 level) is often included in the price. For critical projects, more advanced protection (L7) may be required, which is usually paid separately. Check with your provider what level of protection they provide.
Backup and Snapshot Capabilities
Find out if the provider offers automatic backup services or the ability to create snapshots (instantaneous snapshots of the VPS state). This is crucial for recovery in case of failure or error. However, it is always recommended to have your own backup strategy to external storage.
Initial VPS Server Setup: Basic Steps
After you have ordered a VPS server and received the IP address and root password, you need to perform several basic setup and security steps. Command examples will be for Debian/Ubuntu.
Connecting to VPS via SSH
Use an SSH client (OpenSSH in Linux/macOS, PuTTY or Windows Terminal with built-in SSH in Windows):
ssh root@YOUR_IP_ADDRESSUpon the first connection, you will need to confirm the server’s key fingerprint and enter the password.
System Update
First, update the package lists and installed software:
apt update
apt upgrade -yCreating a New User and Configuring sudo
It is unsafe to work constantly as the root user. Create a regular user and give them sudo privileges:
adduser username
usermod -aG sudo usernameThen log back into the server as the new user.
Basic Firewall Configuration (UFW/firewalld)
Configure the firewall to allow only necessary connections (at least SSH). UFW (Uncomplicated Firewall) is often used for Ubuntu:
sudo ufw allow OpenSSH # or sudo ufw allow 22/tcp
sudo ufw default deny incoming
sudo ufw default allow outgoing
sudo ufw enablefirewalld is used for CentOS/AlmaLinux/Rocky Linux:
sudo systemctl start firewalld
sudo systemctl enable firewalld
sudo firewall-cmd --permanent --add-service=ssh
sudo firewall-cmd --reloadThese are just the very first steps. Further configuration depends on your tasks.
VPS Server Security: Practical Recommendations for Paranoids (and Not Only)
For cybersecurity professionals, this section is especially important. Your VPS server is your fortress on the internet, and it needs to be protected.
Strengthening SSH Access (Keys, Disabling root, Port Change)
- Use SSH keys instead of passwords: This is much safer. Generate a key pair (public and private) on your local computer (
ssh-keygen), copy the public key to the server (ssh-copy-id username@YOUR_IP_ADDRESS). - Disable password login for SSH: In the
/etc/ssh/sshd_configfile, setPasswordAuthentication no. - Disable root login via SSH: In
/etc/ssh/sshd_config, setPermitRootLogin no. - Change the standard SSH port (22): This will reduce the number of automatic bot attacks. In
/etc/ssh/sshd_config, changePort 22to another (e.g.,Port 2222). Don’t forget to allow the new port in the firewall before restarting SSH! - Note: Some consider changing the port «security through obscurity» and not the most effective measure, but it definitely reduces noise in the logs.
- After making changes to
sshd_config, restart the service:sudo systemctl restart sshorsudo systemctl restart sshd.
Configuring Fail2Ban for Brute-Force Protection
Fail2Ban is a utility that scans logs and blocks IP addresses from which multiple unsuccessful login attempts (brute-force) are made to various services (SSH, FTP, web servers, etc.).
sudo apt install fail2ban
sudo systemctl enable fail2ban
sudo systemctl start fail2banCreate a local configuration file for SSH (e.g., /etc/fail2ban/jail.local) and configure the parameters (ban time, number of attempts).
Using Intrusion Detection/Prevention Systems (IDS/IPS)
Consider installing a host-based IDS/IPS such as OSSEC or Wazuh. They will help detect suspicious activity, file changes, and rootkits.
Regular Security Audits and Vulnerability Scanning
- Use tools like Lynis or chkrootkit/rkhunter to audit the system.
- Periodically scan your VPS server with an external vulnerability scanner (e.g., OpenVAS/GVM from another host, or paid services) to identify open ports and known vulnerabilities.
Disabling Unnecessary Services and Hardening Running Ones
Every running service is a potential attack surface. Disable everything that is not used. For running services (web server, database), apply best practices for their «hardening».
Monitoring and Logging
Set up detailed logging and regularly review logs (or use a centralized log collection system). Monitor resource usage (CPU, RAM, disk, network) to detect anomalies in a timely manner.

VPS Server vs. Cloud Platforms (IaaS): Which to Choose?
VPS servers are often compared to virtual machines on large cloud platforms like Amazon Web Services (AWS EC2), Microsoft Azure (Azure VMs), or Google Cloud Platform (GCP Compute Engine). In some ways they are similar (they are all virtual machines), but there are also key differences:
| Parameter | Traditional VPS Server | Cloud VMs (AWS EC2, Azure VM, GCP) |
|---|---|---|
| Payment Model | Fixed monthly/annual fee | Hourly/minutely payment (Pay-as-you-go) + traffic, disks, etc. |
| Ease of Use | Usually simpler control panel, fewer options | More complex ecosystem, many services, steep learning curve |
| Scalability | Vertical (upgrade plan), sometimes horizontal (adding VPS) | High elasticity, automatic scaling (Auto Scaling Groups) |
| Ecosystem of Services | Limited (VPS, DNS, backups) | Huge (databases as a service, storage, AI/ML, serverless, etc.) |
| Network | Simple IP, firewall configuration | Complex virtual networks (VPC/VNet), security groups, load balancers |
| Cost Predictability | High (if you don’t exceed traffic) | Can be low, if you don’t control consumption |
| Support | Depends on the VPS provider | Basic support is free, extended support is paid and expensive |
When to choose a traditional VPS server:
- For projects with predictable load and budget.
- If you need ease of management and don’t need a complex cloud ecosystem.
- For personal projects, small websites, VPNs, test environments.
- If you want to pay a fixed amount per month.
When to choose cloud VMs:
- For projects with highly variable or unpredictable load requiring elastic scaling.
- If you need integrated cloud services (S3, RDS, Lambda, etc.).
- For large applications requiring high availability and geographical distribution.
- If you are willing to invest time in learning the platform and controlling costs.
For many tasks, especially in the field of cybersecurity (personal VPN, small penetration testing lab, honeypot), a traditional VPS server often turns out to be a simpler and more economically viable solution.
The Future of VPS: Trends for 2025 and Beyond
The VPS server market is constantly evolving. In 2025 and beyond, we can expect the following trends:
- NVMe SSD by default: NVMe drives are becoming the standard even for budget VPS, providing a significant increase in disk subsystem performance.
- More powerful CPUs: Providers will offer VPS based on the latest generations of AMD EPYC and Intel Xeon processors, providing more computing power.
- Improved DDoS protection: Against the backdrop of the increasing number and complexity of DDoS attacks, providers will strengthen standard protection measures and offer more advanced paid options.
- Integration with containerization: Simplifying the deployment of Docker containers and Kubernetes clusters (e.g., k3s) on VPS.
- AI/ML in management: AI elements may appear for automated monitoring, resource optimization, and prediction of problems on the provider’s side.
- Edge VPS: Increasing popularity of VPS located at the «edge» of the network (edge locations) to minimize latency for IoT devices and local users.
- Increased focus on security «out of the box»: Providers may offer VPS with pre-installed basic security measures or easily connectable options (e.g., WAF, vulnerability scanners).
Relevant Quote
«Talk is cheap. Show me the code.»
Linus Torvalds (interpretation of his famous phrases in the context of VPS)
…And to show the code in action, you often need a reliable server. And if you add to this: «My name is Linus Torvalds and I am your god.» (when he talks about the Linux kernel), it well conveys the level of control you get with root access on a VPS.
This slightly free interpretation emphasizes that a VPS server gives you the platform and the control (root on a Linux VPS) to implement your projects and ideas as you see fit.
Conclusions
Colleagues, we’ve come a long way together, having thoroughly examined what a VPS server is, how it works, and why it’s needed in the realities of 2025. I hope you now have a complete and comprehensive understanding of this technology.
We learned that:
- A VPS server is a powerful and flexible tool that is the «golden mean» between limited shared hosting and expensive dedicated servers.
- VPS is based on virtualization technology (KVM, Xen, OpenVZ, Hyper-V), which allows you to create isolated virtual machines with guaranteed resources. KVM is often the preferred choice for most tasks.
- The key advantages of VPS are full root control, the ability to install any software, scalability, good performance, and increased security compared to shared hosting.
- The use cases for VPS servers are extremely diverse: from hosting websites and applications to creating VPNs, mail servers, development environments, and, especially important for us, specialized tools for cybersecurity (penetration testing labs, honeypots, malware analysis).
- Choosing a VPS requires attention to detail: virtualization type, resources (CPU, RAM, NVMe SSD), data center location, support quality, and the presence of necessary features (DDoS protection, backups).
- The security of an Unmanaged VPS is entirely your responsibility. We have reviewed basic and advanced steps for server «hardening».
- VPS remains a relevant and sought-after solution even against the backdrop of the rapid development of cloud platforms, offering simplicity and predictability for many tasks.
A VPS server is not just a virtual machine. It is a platform for your projects, a laboratory for experiments, a reliable tool for work and creativity. For a cybersecurity specialist, the ability to choose, configure, and protect a VPS server is one of the fundamental skills. I hope this article was useful and informative for you. Success in your endeavors and secure servers!

