Hello, colleagues! In an era where every click, every connection, and every byte of data can be tracked, analyzed, and, let’s be honest, used not always in our best interests, the issue of digital privacy and security is more critical than ever. Commercial VPN services offer a quick solution, but can we always trust them? Logging policies, potential leaks, «neighbors» on the IP address with a questionable reputation – all this makes you think. But what if I told you that you can take full control of your internet traffic, create your own secure tunnel, and be sure that your data is really yours? Today, we will analyze in detail, step by step, how to set up your own VPN server on a VPS using popular Linux distributions such as Ubuntu. We will cover everything: from choosing the right VPS server for VPN and its initial configuration to deploying protocols like OpenVPN and the super-fast WireGuard VPN on a VPS with Ubuntu. This article is for those who are not afraid of the command line, value control, and want to take their digital security to a new level. Ready to become the master of your traffic? Let’s get started!
Table of Contents
-
Why Your Own VPN on a VPS hosting? Undeniable Advantages
- Choosing the Right VPS Server for VPN: Key Aspects
- Data Center (DC) Geographic Location
- Virtualization Type: KVM – Our Choice
- VPS Resources: RAM, CPU, Disk
- Traffic and Port Speed
- Operating System: Ubuntu/Debian Preferred
- IP Address and IPv6 Support
- Provider Policy and DDoS Protection
- Tips on Renting a VPS for VPN
- VPS Preparation: Initial Setup and Security
- Connecting to the VPS via SSH
- System Update
- Creating an Unprivileged User with sudo
- Basic Firewall Setup (UFW)
- Choosing a VPN Protocol: OpenVPN vs. WireGuard – What’s Better in 2025?
- OpenVPN: A Time-Tested Veteran
- WireGuard: Modern, Fast, and Simple
- Our Recommendation
- Method 1: Setting Up Your Own VPN Server on a VPS with OpenVPN (Ubuntu/Linux)
- Installing OpenVPN Using a Script (Recommended Method)
- Manual OpenVPN Installation (For In-depth Understanding – Optional)
- Setting Up OpenVPN Clients
- Method 2: Setting Up WireGuard VPN on a VPS with Ubuntu (and other Linux)
- Checking Kernel Support and Installation
- Installing WireGuard Using a Script (Recommended Method)
- Manual WireGuard Setup (Detailed Guide)
- Generating Keys and Configuring the WireGuard Server
- Configuring IP Forwarding and Firewall for WireGuard
- Generating Keys and Configuring WireGuard Clients
- Adding Peers (Clients) to the Server
- Setting Up WireGuard Clients
- Advanced Settings and Best Practices for Your VPN Server
- Preventing DNS Leaks
- Implementing a Kill Switch
- Using a Non-Standard Port
- IPv6 Support in VPN
- Setting Up Split Tunneling
- Troubleshooting Common VPN Server Issues
- Strengthening the Security of Your VPS Server for VPN
- VPS Security
- VPN Protocol Security
- Your Logging Policy
- Legal and Ethical Aspects of Using Your Own VPN
- Relevant Quote
- Conclusions: Your Own VPN – Freedom and Control
Why Your Own VPN on a VPS? Undeniable Advantages
Before we delve into the technical details of setting up your own VPN server on a VPS, let’s clearly define why this is worth your effort. After all, the market is full of ready-made VPN services, both paid and free. So, what’s the point?
- Full Control and No Logs (at your discretion): This is perhaps the main argument. When you use a commercial VPN, you entrust your data to a third party. They promise «no logs»? Maybe. But it’s practically impossible to verify this. Your own VPS server for VPN means that only you decide what logs are kept (or not kept at all). You are the master of the server and the data.
- Maximum Privacy and Security: All traffic between your device and the VPS is encrypted with reliable algorithms. This protects you from eavesdropping by your internet provider, on public Wi-Fi networks, and from many types of «man-in-the-middle» attacks. You choose the protocol and encryption level yourself.
- Bypassing Geo-restrictions and Censorship: By choosing a VPS server for VPN in the desired country, you get an IP address of that country. This opens access to content blocked in your region and allows you to bypass government censorship.
- Dedicated IP Address (most often): Many commercial VPNs provide shared IP addresses that may be blacklisted due to the actions of other users. With your VPS, you usually get a clean, dedicated IP address (or several).
- Cost-effectiveness (in some cases): If you need a VPN for several devices or a small team, the cost of renting a VPS for VPN may be lower than multiple subscriptions to premium VPN services.
- Configuration Flexibility: You can configure the VPN server precisely to your needs: choose ports, protocols, configure DNS, specific routes, connect multiple devices.
- Invaluable Experience and Knowledge: The process of setting up and administering your own VPN server is a great opportunity to deepen your knowledge in network technologies, Linux, and cybersecurity. For a specialist, this is always a plus.
- Using the VPS for Other Purposes: Your VPS server for VPN does not have to be only a VPN server. You can host a small website, a test environment, a bot, or something else (within reason and without interfering with the VPN’s operation).
Of course, there is a downside: responsibility for setup, maintenance, and security falls entirely on you. But for those who value the advantages listed above, this is not an obstacle, but an interesting challenge.
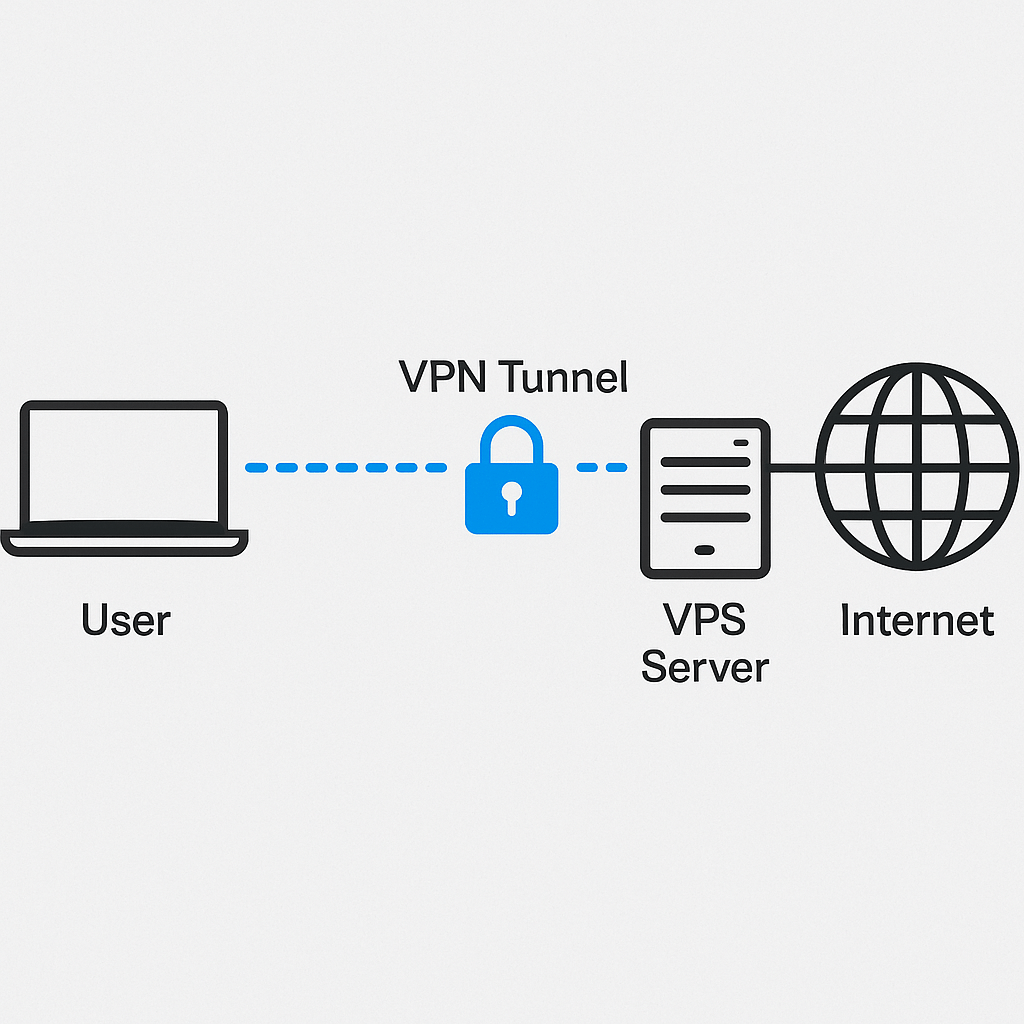
Choosing the Right VPS Server for VPN: Key Aspects
Choosing the right VPS server for VPN is the foundation of your future VPN. The speed, stability, and functionality of your secure tunnel depend on the correctness of this choice. Let’s consider what to pay close attention to when renting a VPS for VPN.
Data Center (DC) Geographic Location
This is one of the most critical parameters. The location of your VPS server for VPN affects:
- Connection speed and ping: The closer the server is to you physically, the lower the latency (ping) will be and, as a rule, the higher the speed. If your main goal is simply safe browsing from your current location, choose a DC in your country or the nearest neighboring one. Bypassing geo-restrictions: If you want to access content available only in a specific country (for example, US servers or European streaming services), then you need to choose a VPS in that country.
- Legislation and privacy policy: Countries with lenient legislation regarding data privacy (for example, some European countries, offshore jurisdictions) may be preferable if this is critical to you. Avoid countries with strict censorship or mandatory logging.
Virtualization Type: KVM – Our Choice
We have already touched on this in previous articles, but for VPN this is especially important. There are various virtualization technologies, but for a VPN server, it is strongly recommended to choose KVM (Kernel-based Virtual Machine).
- KVM: Provides full (hardware) virtualization. This means that your VPS gets its own isolated operating system kernel. This is critical for:
- Guaranteed operation of kernel modules necessary for VPN, such as TUN/TAP (for OpenVPN) or the WireGuard module (if it is not built into the provider’s main kernel).
- Ability to install any OS and fully configure it.
- Better resource isolation and stability.
- OpenVZ: This is container virtualization. All VPSs on OpenVZ use the shared kernel of the host machine. This can lead to problems:
- Lack of necessary TUN/TAP modules or their reduced functionality (if the provider hasn’t taken care of it).
- Inability to load your own kernel module (for example, for WireGuard on older systems where it is not included in the host kernel).
- Potential «overselling» of resources by the provider.
Verdict: For a VPS server for VPN always prefer KVM virtualization. Xen (HVM) is also a good alternative. Avoid OpenVZ if there is a choice.
VPS Resources: RAM, CPU, Disk
Good news: VPN servers (especially WireGuard) are not very demanding on resources for servicing several users.
- RAM (Random Access Memory):
- For WireGuard and a small number of clients (1-5), 256-512 MB RAM is often sufficient.
- For OpenVPN, 512 MB is recommended, preferably 1 GB, especially if many simultaneous connections or resource-intensive ciphers are planned.
- Keep in mind that the OS itself (e.g., Ubuntu Server) consumes some amount of RAM (100-200 MB idle).
- Recommendation: Start with 512 MB — 1 GB RAM for a KVM VPS. This should be enough for most personal VPN tasks.
- CPU (Processor):
- 1 vCPU (virtual core) is usually enough. VPN encryption, of course, loads the processor, but modern CPUs (even virtual ones) handle this well, especially with AES-NI (hardware AES acceleration), which is supported by most modern processors and VPN protocols. WireGuard uses ChaCha20, which is also very fast.
- If you plan hundreds of simultaneous connections or very intensive traffic, you may need 2 vCPUs. Disk: The VPN server itself takes up very little space. Linux OS (Ubuntu Server minimal) + VPN software is usually up to 5-10 GB. Disk type: SSD (Solid State Drive) or NVMe servers SSD is preferable to HDD for overall system responsiveness, although for VPN this is not as critical as for a web server or database. However, most providers now offer SSD by default. Volume: 10-20 GB SSD is more than enough for a dedicated VPN server.
Traffic and Port Speed
-
Port speed: Providers usually offer 100 Mbps, 200 Mbps, 1 Gbps, or even 10 Gbps dedicated servers ports. 100 Mbps may be enough for a personal VPN, but if possible and budget allows, 1 Gbps will provide a better experience (especially if you plan to download large files via VPN). The actual speed will depend on many factors, including the provider’s network load and the route to you.
- Traffic volume: Many providers offer «unlimited» traffic at a certain port speed, but always read the fine print (there may be «fair use policy» restrictions). Others offer limited traffic volume per month (e.g., 1 TB, 2 TB, 5 TB). Assess your needs. For regular browsing, email, and messengers, 1 TB per month is a lot. If you plan to watch a lot of streaming video or download torrents (be careful with the law!), you will need more.
Operating System: Ubuntu/Debian Preferred
For setting up your own VPN server on a VPS, we recommend using the latest LTS (Long-Term Support) versions of popular Linux distributions:
- Ubuntu Server (LTS): For example, 20.04 LTS, 22.04 LTS. Excellent community, lots of documentation, fresh packages. Ideal for WireGuard VPN on a VPS with Ubuntu, as WireGuard is included in the kernel in the latest versions. Download/Select when ordering VPS.
- Debian: Stable, reliable, low resource consumption. Also an excellent choice. Download/Select when ordering VPS.
- CentOS Stream / AlmaLinux / Rocky Linux: Also suitable, but installing some packages or scripts may differ slightly.
Make sure the provider allows you to install a clean OS without unnecessary pre-installed software.
IP Address and IPv6 Support
- Dedicated static IPv4 address: This is an absolute necessity for a VPN server.
- IPv6 support: It is desirable that your VPS server for VPN also has an IPv6 address. This will allow you to configure the VPN to work with IPv6 traffic as well, which is becoming increasingly relevant.
Provider Policy and DDoS Protection
- Terms of Service (ToS): Carefully read the provider’s ToS. Make sure they allow running VPN servers. Most adequate providers allow this. Also pay attention to the policy regarding traffic (DMCA, torrents, etc.).
- DDoS protection: Basic DDoS protection from the provider is a plus. It can help to repel simple attacks targeting your IP address. For VPN, this is not as critical as for a public web server, but still useful.
Tips on Renting a VPS for VPN
- Read reviews: Before renting a VPS for VPN, look for recent reviews of the provider on independent platforms (e.g., LowEndTalk, Trustpilot, specialized forums). Pay attention to stability, support quality, and the correspondence of the declared characteristics to the real ones.
- Don’t chase the lowest price: Too cheap VPSs may mean overselling, unstable operation, or poor network quality. Look for a balance of price and quality.
- Trial period or money-back guarantee: The presence of a trial period or a money-back guarantee is a good sign. You will be able to check if the VPS suits you before paying for a long term.
- Payment methods: Make sure the provider accepts convenient payment methods for you (cards, PayPal, cryptocurrencies for anonymity).

VPS Preparation: Initial Setup and Security
So, you have chosen and paid for your VPS server for VPN. The provider has sent you the IP address, username (usually root), and password. Before installing VPN software, you need to perform several important steps to initially set up and basically strengthen the security of your server. Examples of commands are given for Ubuntu/Debian.
Connecting to the VPS via SSH
To connect to your VPS, use an SSH client. On Linux and macOS, this is the standard ssh utility. On Windows, you can use PuTTY, Windows Terminal (with its built-in OpenSSH client), or WSL (Windows Subsystem for Linux).
ssh root@YOUR_VPS_IP_ADDRESSUpon the first connection, you will be prompted to verify the server’s key fingerprint. Compare it to the one your provider may have given you (if they provided one), and type yes. Then enter the password provided by your provider.
System Update
Immediately after logging in, the first thing you should do is update the package lists and all installed software to the latest versions. This will close known vulnerabilities.
sudo apt update
sudo apt upgrade -yIf during apt upgrade the system prompts you to update configuration files, carefully read what is changing. Most often, you can choose the option «install the package maintainer’s version» if you haven’t manually changed anything yet.
Creating an Unprivileged User with sudo
Constantly working as the root user is bad security practice. Let’s create a new user and give them the ability to run commands with elevated privileges via sudo.
adduser your_usernameThe system will prompt you to enter a password for the new user and some additional information (you can leave it blank by pressing Enter). Then, let’s add the new user to the sudo group:
usermod -aG sudo your_usernameNow exit the root session (exit command) and log in to the server as the new user:
ssh your_username@YOUR_VPS_IP_ADDRESSCheck that sudo works by running, for example, sudo apt update. The system will prompt for your user’s password.
It is strongly recommended to also configure SSH key authentication and disable password login, as well as root login via SSH. This will significantly improve the security of your server. We have covered this in detail in other articles, but briefly:
1. Generate SSH keys on your local computer: ssh-keygen -t rsa -b 4096 (or ed25519).
2. Copy the public key to the server: ssh-copy-id your_username@YOUR_VPS_IP_ADDRESS.
3. Check that you can log in with the key without a password.
4. On the server, edit the /etc/ssh/sshd_config file:
sudo nano /etc/ssh/sshd_config
Set:
PasswordAuthentication no
PermitRootLogin no
PubkeyAuthentication yes
5. Restart the SSH service: sudo systemctl restart ssh or sudo systemctl restart sshd.
Warning: Before disabling password login, make sure that key login is working correctly, otherwise you may lose access to the server!
Basic Firewall Configuration (UFW)
A firewall is the first line of defense. UFW (Uncomplicated Firewall) is a convenient wrapper for iptables, pre-installed in many Ubuntu distributions. Let’s configure it to block all incoming connections by default, except those that we explicitly allow.
sudo ufw default deny incoming
sudo ufw default allow outgoingLet’s allow SSH connections (if you changed the standard SSH port, specify it instead of 22):
sudo ufw allow ssh # This will allow port 22 by default
# or, if you changed the port to, for example, 2222:
# sudo ufw allow 2222/tcpLater we will add rules to allow traffic from our VPN server. Let’s activate UFW:
sudo ufw enableThe system will warn that this may disrupt current SSH connections. Enter y. Let’s check the status:
sudo ufw status verboseYou should see that the firewall is active and only SSH connections (and outgoing ones) are allowed.
This completes the basic preparation of a VPS server for VPN. It is now ready for VPN software installation.
VPN Protocol Choice: OpenVPN vs. WireGuard – Which is Better in 2025?
The two most popular and recommended protocols for setting up your own VPN server on a VPS are OpenVPN and WireGuard. Each has its strengths and weaknesses.
OpenVPN: A Time-Tested Veteran
- Pros:
- Maturity and Reliability: OpenVPN has been around for a long time, its code has been repeatedly tested and audited. It is considered very secure.
- High Configurability: A huge number of settings allow fine-tuning to suit any needs (choice of ciphers, authentication, ports, TCP/UDP protocols).
- TCP and UDP Support: Can work both via UDP (faster, preferred) and TCP (more reliable, can bypass some firewalls by masquerading as HTTPS on port 443).
- Wide Platform Support: OpenVPN clients are available for almost all operating systems and devices.
- Obfuscation: There are methods for masking OpenVPN traffic (e.g., through Stunnel or obfsproxy), which helps bypass advanced DPI (Deep Packet Inspection) systems in countries with strict censorship.
- Cons:
- Performance: Can be slower than WireGuard, especially on weak devices, due to higher overhead and user-space operation (although DCO — Data Channel Offload — improves this).
- Complexity of Setup: Manual configuration of OpenVPN «from scratch» (with the generation of all certificates and keys) is a rather laborious process.
- Large Codebase: Theoretically, the more code, the higher the probability of vulnerabilities (although OpenVPN is well-audited).
WireGuard: Modern, Fast, and Simple
- Pros:
- High Performance: WireGuard is significantly faster than OpenVPN due to kernel-space operation and the use of modern efficient cryptographic primitives (ChaCha20, Poly1305, Curve25519).
- Ease of Setup: WireGuard configuration is much simpler and more intuitive than OpenVPN. Fewer parameters, easier to understand.
- Compact Codebase: Significantly fewer lines of code (about 4000), which simplifies auditing and reduces the attack surface.
- Modern Cryptography: Uses advanced, secure, and fast algorithms by default, without the ability to choose less secure options («opinionated cryptography»).
- Built into the Linux Kernel: Starting with kernel version 5.6, WireGuard is part of the Linux kernel, simplifying its installation and providing better performance. Many distributions (including recent Ubuntu versions) come with WireGuard support «out of the box».
- Roaming and IP Changes: Better handles client IP address changes or switching between networks (Wi-Fi, mobile) without connection interruption.
- Cons:
- UDP Only: WireGuard works exclusively over the UDP protocol. This can be a problem in networks where UDP traffic is blocked or severely restricted (e.g., some corporate or public Wi-Fi networks). OpenVPN with TCP wins here.
- Less «Mature» (Relatively): Although WireGuard has already proven itself and has undergone audits, it is still younger than OpenVPN.
- Dynamic IP Allocation (Requires Additional Tools): WireGuard itself does not manage dynamic IP address allocation to clients in the same way that OpenVPN does. IP addresses are usually statically specified in the peer configuration. Third-party scripts or tools may be needed for automation.
- Obfuscation is More Difficult: Masking WireGuard traffic is more difficult than for OpenVPN, although it is possible (e.g., through udp2raw or other tunneling utilities).
Our Recommendation
In 2025, for most users setting up their first VPS server for VPN, we recommend starting with WireGuard. Its simplicity, speed, and modern security make it an excellent choice, especially if your VPS server for VPN runs on a recent version of Ubuntu where WireGuard support is already in the kernel.
OpenVPN remains an excellent choice if:
- You need to work through TCP (e.g., to bypass firewalls blocking UDP).
- You require very specific encryption or authentication settings.
- You need advanced traffic obfuscation methods.
- You simply trust a time-tested solution more.
Nothing prevents you from installing both protocols on one VPS server for VPN and using them for different purposes or as a backup.

Method 1: Setting up your own VPN server on a VPS with OpenVPN (Ubuntu/Linux)
Despite our recommendation in favor of WireGuard for beginners, OpenVPN is still very popular and reliable. Let’s look at how to install it.
Installing OpenVPN Using a Script (Recommended Method)
Manual OpenVPN configuration, including creating a Certificate Authority (CA), generating server and client certificates and keys, and writing configuration files, can be complex and error-prone. Fortunately, there are excellent automated scripts that do 99% of the work for you. One of the most popular and proven is the script from Nyr.
Step 1: Downloading and Running the Script
Connect to your VPS server for VPN via SSH as a user with sudo privileges. Then run the following commands:
wget https://git.io/vpn -O openvpn-install.sh
chmod +x openvpn-install.sh
sudo ./openvpn-install.shStep 2: Answering the Script’s Questions
The script will ask you several questions to configure the OpenVPN server:
- IP address: The script usually automatically detects your VPS’s public IP address. If you have multiple IPs, choose the one you need. Press Enter if the suggested option is correct.
- IPv6 support: If your VPS has IPv6 and you want to use it, choose ‘y’.
- Port: The port for OpenVPN. The default is
1194. You can leave it or choose another (e.g.,443if you want to masquerade as HTTPS, but make sure port 443 is not used by another service, such as a web server, and select TCP below). - Protocol:
UDPorTCP. UDP is usually faster, TCP is more reliable and better at bypassing firewalls. For most cases, UDP is the best choice. - DNS servers: Which DNS servers clients will use when connecting to the VPN. You can choose from the suggested ones (Google, Cloudflare, Quad9, etc.) or specify your own. Cloudflare (
1.1.1.1) or Google (8.8.8.8) are good options. - Enable compression? Compression can slightly reduce the amount of data transferred, but it can also increase CPU load and be vulnerable to VORACLE-type attacks. Modern recommendations often advise against compression (
n). - Customize encryption settings? For most users, the default encryption settings offered by the script will be strong and secure enough. If you are unsure, choose
n.
After answering all the questions, the script will install OpenVPN, generate the necessary certificates and keys, configure the server, and firewall rules (UFW or firewalld).
Step 3: Creating a Client Configuration File (.ovpn)
Upon completion of the installation, the script will prompt you to create the first client profile:
- Client name: Enter a name for the client (e.g.,
myphone,laptop). - Protect the configuration file with a password? You can protect the
.ovpnfile with a password. If you choosey, you will need to enter this password each time you connect the client. For convenience, you can choosen, but then keep the.ovpnfile itself secure.
The script will create an .ovpn file (e.g., /home/your_username/myphone.ovpn). This file must be securely copied from your VPS server for VPN to the device that will connect to the VPN (e.g., using scp, FileZilla, or simply outputting the file content with the command cat /home/your_username/myphone.ovpn and copying the text to a file on your local machine).
Step 4: User Management (Adding/Removing)
To add a new user or remove an existing one, simply run the script again:
sudo ./openvpn-install.shThe script will detect that OpenVPN is already installed and will offer a menu: 1. Add a new client 2. Revoke an existing client 3. Remove OpenVPN 4. Exit
Select the desired option.
Manual OpenVPN Installation (For Deeper Understanding – Optional)
Manually setting up OpenVPN is a complex process that goes beyond the scope of this article if described in full detail to reach the required character count. However, for cybersecurity professionals who want to understand all the nuances, the main steps look like this:
- Installing OpenVPN and Easy-RSA:
sudo apt install openvpn easy-rsa - Configuring Easy-RSA: Copy the Easy-RSA directory (
make-cadir ~/openvpn-ca), edit thevarsfile with your CA data. - Creating a Certificate Authority (CA): Initialize PKI (
./easyrsa init-pki), create CA (./easyrsa build-ca nopass). - Generating the server certificate and key: Create a server certificate request (
./easyrsa gen-req server nopass), sign the request (./easyrsa sign-req server server). - Generating Diffie-Hellman parameters:
./easyrsa gen-dh. - Generating an HMAC key for DoS protection (tls-auth/tls-crypt):
openvpn --genkey --secret ta.key. - Generating certificates and keys for clients: Similar to the server, but for each client (
./easyrsa gen-req client1 nopass,./easyrsa sign-req client client1). - Copying the necessary files to the OpenVPN directory (
/etc/openvpn):ca.crt,server.crt,server.key,dh.pem,ta.key. - Creating the server configuration file (
/etc/openvpn/server.conf): Specify the port, protocol, device (tun), paths to certificates and keys, VPN network parameters (server 10.8.0.0 255.255.255.0), push options for clients (routes, DNS), ciphers (cipher AES-256-GCM,auth SHA256), keepalive, user/group, etc. Example of key lines:port 1194 proto udp dev tun ca ca.crt cert server.crt key server.key dh dh.pem tls-auth ta.key 0 # Server server 10.8.0.0 255.255.255.0 ifconfig-pool-persist ipp.txt push "redirect-gateway def1 bypass-dhcp" push "dhcp-option DNS 1.1.1.1" push "dhcp-option DNS 1.0.0.1" keepalive 10 120 cipher AES-256-GCM auth SHA256 user nobody group nogroup persist-key persist-tun status openvpn-status.log verb 3 - Setting up IP forwarding:
sudo sysctl -w net.ipv4.ip_forward=1Uncomment the linenet.ipv4.ip_forward=1in/etc/sysctl.confto save after reboot. - Firewall (NAT) configuration: This is a critical step to allow VPN clients to access the internet through the server.
Example for UFW (in addition to allowing the OpenVPN port):
In the
/etc/ufw/before.rulesfile, before the*filterline, add:
Replace*nat :POSTROUTING ACCEPT [0:0] -A POSTROUTING -s 10.8.0.0/24 -o YOUR_VPS_NETWORK_INTERFACE -j MASQUERADE COMMITYOUR_VPS_NETWORK_INTERFACEwith the name of your main network interface (e.g.,eth0,ens3– you can find it using the commandip addr). In the/etc/default/ufwfile, setDEFAULT_FORWARD_POLICY="ACCEPT". Reload UFW:sudo ufw disable && sudo ufw enable. Allow the OpenVPN port:sudo ufw allow 1194/udp(or whichever port and protocol you chose). - Starting and enabling OpenVPN autostart:
sudo systemctl start openvpn@serversudo systemctl enable openvpn@server - Creating client .ovpn files: Combine
ca.crt,client.crt,client.key,ta.key(if used) into a single file and add configuration directives (client,dev tun,proto udp,remote YOUR_VPS_IP_ADDRESS 1194,resolv-retry infinite,nobind,persist-key,persist-tun,remote-cert-tls server,cipher AES-256-GCM,auth SHA256,verb 3, etc.). The contents of the keys and certificates are inserted directly into the file between the tags<ca>...</ca>,<cert>...</cert>,<key>...</key>,<tls-auth>...</tls-auth>.
As you can see, manual configuration requires considerable effort and attention to detail. Using scripts greatly simplifies life and reduces the risk of errors.
OpenVPN Client Setup
Once you have the .ovpn file, you need to import it into the OpenVPN client application on your device.
- Windows: OpenVPN Community Client or OpenVPN Connect. After installation, import the
.ovpnfile. - macOS: Tunnelblick (a popular free client) or the official OpenVPN Connect.
- Linux: You can use NetworkManager with the
network-manager-openvpn-gnome(for Gnome) ornetwork-manager-openvpnplugin, or the command-line clientopenvpn(sudo openvpn --config /path/to/file.ovpn). - Android: OpenVPN Connect from Google Play.
- iOS: OpenVPN Connect from the App Store.
After importing the profile, simply click «Connect». If everything is configured correctly, you will connect to your VPS server for VPN. Check your IP address (it should be the IP address of your VPS) and internet accessibility.
Method 2: Setting up WireGuard VPN on a VPS with Ubuntu (and other Linux distributions)
WireGuard is our favorite for quickly and easily setting up your own VPN server on a VPS. It is especially well-suited for WireGuard VPN on a VPS with Ubuntu, as the latest Ubuntu versions have built-in support.
Checking Kernel Support and Installation
Starting with the Linux 5.6 kernel, WireGuard is part of it. Check your kernel version:
uname -rIf the version is 5.6 or higher, great. If lower (for example, on older LTS Ubuntu 18.04, which may have kernel 4.x or 5.4 HWE), you may need to install WireGuard via PPA or as a DKMS module. However, most modern VPS providers will offer you Ubuntu 20.04 LTS, 22.04 LTS or newer, where there should be no kernel issues.
In any case, install the WireGuard utilities:
sudo apt update
sudo apt install wireguard resolvconf # resolvconf for managing DNS via wg-quick (optional, but useful)Installing WireGuard using a Script (Recommended Method)
As with OpenVPN, there are convenient scripts for automatic installation of WireGuard. One of the popular ones is the script from angristan. It greatly simplifies the process of setting up a WireGuard VPN on a VPS with Ubuntu.
Step 1: Downloading and running the script
curl -O https://raw.githubusercontent.com/angristan/wireguard-install/master/wireguard-install.sh
chmod +x wireguard-install.sh
sudo ./wireguard-install.shStep 2: Answering the script’s questions
The script will also ask a few questions:
- Public IPv4 or IPv6 address for the server: Usually determined automatically.
- Public network interface: Usually
eth0orens3, determined automatically. - WireGuard interface name: Defaults to
wg0. Can be left as is. - Server’s WireGuard IPv4: Server’s IP address in the VPN subnet (e.g.,
10.66.66.1/24). - Server’s WireGuard IPv6 (optional): If you have IPv6 on the VPS.
- Port for WireGuard: UDP port for WireGuard. Defaults to
51820. Can be changed. - DNS server for the clients: Which DNS servers the clients will use.
- Enable unattended-upgrades? Automatic security updates for the system. Recommended (
y).
After installation, the script will offer to create the first client:
- Client name: Client name.
- Client’s WireGuard IPv4: Client’s IP address in the VPN subnet (e.g.,
10.66.66.2/32). - Client’s WireGuard IPv6 (optional).
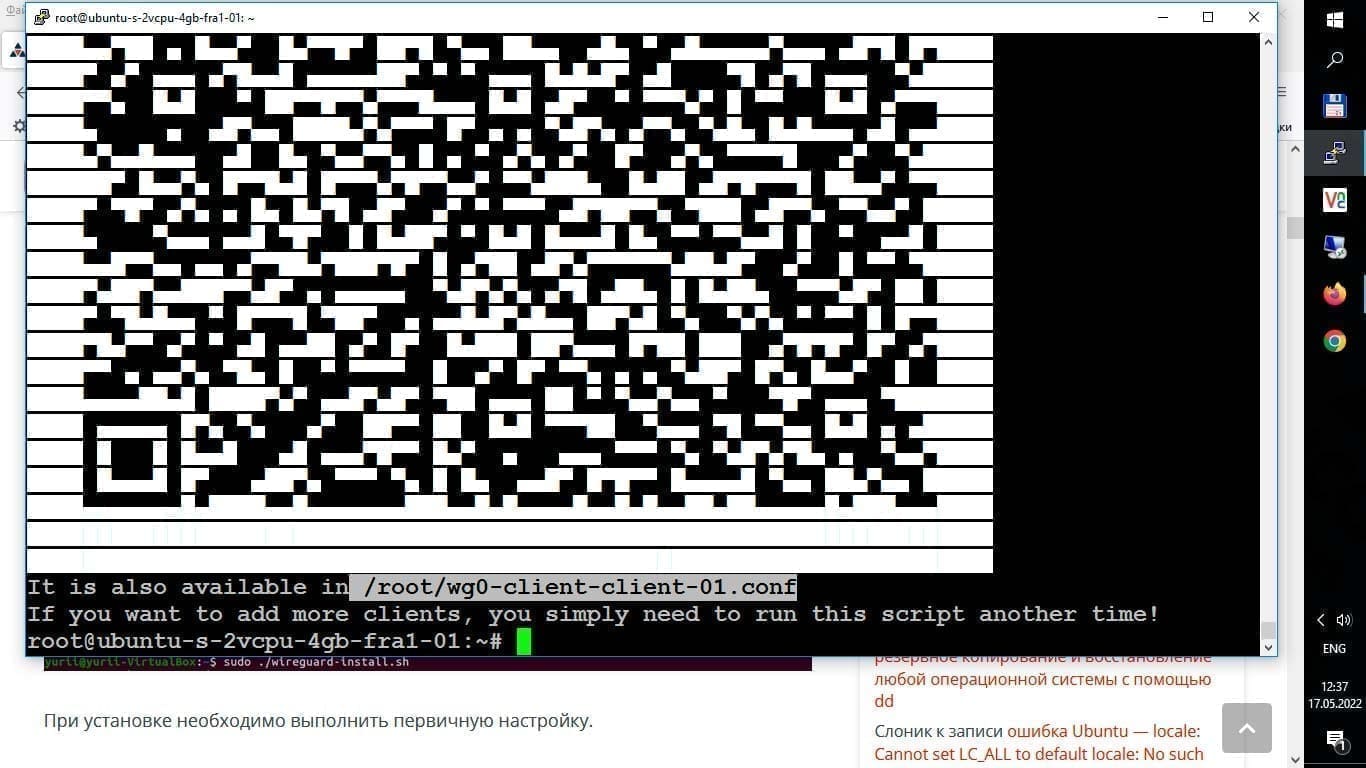
The script will generate a .conf configuration file for the client (e.g., /home/your_username/wg0-client-myphone.conf) and a QR code for easy setup on mobile devices.
Step 3: Managing users
To add/remove clients, simply run the script again: sudo ./wireguard-install.sh. It will offer a management menu.
Manual WireGuard Setup (Detailed Guide)
If you want complete control and understanding, here’s how to manually configure WireGuard VPN on a VPS with Ubuntu. This is slightly more complex than the script, but provides more flexibility and knowledge.
Generating Keys and Configuring the WireGuard Server
1. Generating a key pair for the server:
wg genkey | sudo tee /etc/wireguard/server_private.key
sudo chmod 600 /etc/wireguard/server_private.key
sudo cat /etc/wireguard/server_private.key | wg pubkey | sudo tee /etc/wireguard/server_public.keySave the private key (server_private.key) in a safe place; you will need it for configuration. The public key (server_public.key) will be used by clients.
2. Creating the server configuration file:
Create the file /etc/wireguard/wg0.conf (wg0 is the interface name; it can be anything, but wg0 is standard):
sudo nano /etc/wireguard/wg0.confPaste the following content, replacing the values with your own:
[Interface]
Address = 10.10.0.1/24 # Server IP address in the VPN network and subnet mask
# Address = fd42:42:42::1/64 # Optional IPv6 address of the server in the VPN network
SaveConfig = true # Allows saving changes made via 'wg set'
ListenPort = 51820 # UDP port that WireGuard will listen on
PrivateKey = YOUR_SERVER_PRIVATE_KEY # Paste the contents of /etc/wireguard/server_private.key
# These lines are responsible for NAT, so that clients can access the internet via VPN.
# Replace 'eth0' with your main network interface (find out: ip -br a)
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip6tables -A FORWARD -i %i -j ACCEPT; ip6tables -t nat -A POSTROUTING -o eth0 -j MASQUERADE # For IPv6, if used
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PostDown = ip6tables -D FORWARD -i %i -j ACCEPT; ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE # For IPv6, if used
# Next will be [Peer] sections for each clientSet the correct permissions for the configuration file:
sudo chmod 600 /etc/wireguard/wg0.confSetting up IP Forwarding and the Firewall for WireGuard
1. Enabling IP forwarding:
For the server to route client traffic, you need to enable IP forwarding:
sudo sysctl -w net.ipv4.ip_forward=1
sudo sysctl -w net.ipv6.conf.all.forwarding=1 # If using IPv6To save the changes after reboot, edit /etc/sysctl.conf:
sudo nano /etc/sysctl.confUncomment (or add) the lines:
net.ipv4.ip_forward=1
net.ipv6.conf.all.forwarding=1 # If using IPv6Apply the changes: sudo sysctl -p.
2. Firewall (UFW) configuration:
Allow incoming connections on the WireGuard port (e.g., 51820/udp):
sudo ufw allow 51820/udpWe have already added NAT (MASQUERADE) rules to the PostUp/PostDown sections of the wg0.conf file; they will be applied automatically when the wg0 interface is started/stopped. However, forwarding also needs to be allowed for UFW. Edit /etc/default/ufw:
sudo nano /etc/default/ufwChange DEFAULT_FORWARD_POLICY="DROP" to DEFAULT_FORWARD_POLICY="ACCEPT".
Reload UFW: sudo ufw disable && sudo ufw enable.
Generating Keys and Configuring WireGuard Clients
For each client, you need to generate a key pair and create a configuration file.
1. Generating client keys (can be done on the server or on the client):
wg genkey | tee client1_private.key
cat client1_private.key | wg pubkey | tee client1_public.keySave the client’s private key (client1_private.key) – it will go into the client’s configuration. The public key (client1_public.key) needs to be added to the server.
2. Creating the client configuration file (e.g., client1.conf):
[Interface]
PrivateKey = YOUR_CLIENT_PRIVATE_KEY
Address = 10.10.0.2/32 # Unique client IP address in the VPN network
# Address = fd42:42:42::2/128 # Optional IPv6 client address
DNS = 1.1.1.1, 8.8.8.8 # DNS servers for the client
[Peer]
PublicKey = YOUR_SERVER_PUBLIC_KEY # From /etc/wireguard/server_public.key
Endpoint = YOUR_VPS_IP_ADDRESS:51820
AllowedIPs = 0.0.0.0/0, ::/0 # Route all traffic through the VPN
PersistentKeepalive = 25 # Optional, for maintaining the connection behind NATThis client1.conf file needs to be transferred to the client device.
Adding Peers (Clients) to the Server
Now, on the server, you need to «tell» WireGuard about the client. Add a [Peer] section to the /etc/wireguard/wg0.conf file for each client:
# This is added to /etc/wireguard/wg0.conf AFTER the [Interface] section
[Peer]
PublicKey = CLIENT1_PUBLIC_KEY # From client1_public.key
AllowedIPs = 10.10.0.2/32 # IP address from which this client is allowed
# AllowedIPs = 10.10.0.2/32, fd42:42:42::2/128 # If using IPv6Repeat for each client, changing the public key and AllowedIPs.
3. Starting the WireGuard server:
sudo systemctl enable wg-quick@wg0 # Enable autostart
sudo systemctl start wg-quick@wg0 # Start nowCheck the status:
sudo systemctl status wg-quick@wg0
sudo wg show # Should show the wg0 interface, its public key, port, and peer information (after they connect)If you made changes to wg0.conf after starting, restart the service: sudo systemctl restart wg-quick@wg0.
Setting up WireGuard Clients
WireGuard clients are available for all major platforms. Download the official client from wireguard.com/install/.
- Windows, macOS, Linux: Install the client and import the
.conffile. - Android, iOS: Install the app from Google Play or the App Store. You can import the configuration from the
.conffile or by scanning the QR code (if you generated one, for example, using the commandqrencode -t ansiutf8 < client1.confon the server, ifqrencodeis installed).
After importing and activating the profile, check your IP address and internet access.
Advanced Settings and Best Practices for Your VPN Server
After the basic setup of your own VPN server on a VPS, you can consider several advanced options to improve its performance and security.
Preventing DNS Leaks
A DNS leak occurs when DNS queries from your device go outside the VPN tunnel to your provider’s DNS servers. This can reveal your activity. Make sure that VPN clients use the DNS servers specified in the VPN configuration.
- OpenVPN: Use the
push "dhcp-option DNS DNS_IP_ADDRESS"directive inserver.conf. For example,push "dhcp-option DNS 1.1.1.1". For Windows clients,push "block-outside-dns"may be required. - WireGuard: Specify
DNS = DNS_IP_ADDRESSin the[Interface]section of the client’s.conffile.
You can check for DNS leaks on sites like dnsleaktest.com.
Implementing a Kill Switch
A Kill Switch is a feature that blocks all internet traffic if the VPN connection suddenly drops. This prevents your real IP address from leaking.
- Client-side: Some VPN clients (e.g., the official OpenVPN client for Windows) have a built-in Kill Switch feature.
- Client-side firewall: You can configure your client device’s firewall to allow traffic only through the VPN interface or to the VPN server’s IP address. This is a more complex setup.
Using a Non-Standard Port
Standard VPN ports (1194 for OpenVPN, 51820 for WireGuard) may be blocked on some networks. Using a non-standard port (e.g., 443/tcp for OpenVPN to masquerade as HTTPS, or any other free UDP port for WireGuard) can help bypass such blocks. Remember to update the firewall rules on the server.
IPv6 Support in VPN
If your VPS for VPN and your local network support IPv6, configure the VPN to route IPv6 traffic. This will provide access to IPv6 resources and prevent IPv6 leaks (where IPv4 goes through the VPN, but IPv6 goes directly).
- OpenVPN: Use
server-ipv6 IPV6_SUBNETinserver.confandpush "route-ipv6 2000::/3"(or a more specific route). - WireGuard: Add IPv6 addresses to the
Addresssection on the server and clients, andAllowedIPs = ..., ::/0on the client. Ensure that thePostUp/PostDownrules forip6tablesare correct.
Configuring Split Tunneling
By default, all client traffic goes through the VPN. Split tunneling allows you to configure it so that only specific traffic (e.g., to certain websites or IP addresses) goes through the VPN, while the rest goes directly. This can be useful for accessing local network resources or saving VPN traffic.
- OpenVPN: You can manage routes using
push "route IP_ADDRESS MASK"and not usingredirect-gateway. - WireGuard: In the client
.conffile, in the[Peer]section, theAllowedIPsparameter determines which traffic will be routed through the VPN. Instead of0.0.0.0/0, ::/0, specify specific subnets.
Troubleshooting Common VPN Server Issues
Even with careful setup of your own VPN server on a VPS, problems can arise. Here are some common ones and how to solve them:
- Client cannot connect to the VPN server:
- Check the VPN service status on the VPS:
For OpenVPN:
sudo systemctl status openvpn@server(or the name of your service). For WireGuard:sudo systemctl status wg-quick@wg0andsudo wg show. Restart if not active:sudo systemctl restart .... - Check the VPS firewall: Make sure the VPN port (e.g., 1194/udp for OpenVPN, 51820/udp for WireGuard) is open for incoming connections.
sudo ufw status verbose. - Check the VPN server logs:
For OpenVPN:
sudo journalctl -u openvpn@serveror the log file specified inserver.conf(status openvpn-status.log,log /var/log/openvpn.log). For WireGuard:sudo dmesg | grep wireguardorsudo journalctl -u wg-quick@wg0. - Check the client configuration: Is the server’s IP address/domain, port, keys/certificates correct?
- Check the network connection to the VPS: Try simply pinging the VPS IP address (
ping YOUR_VPS_IP_ADDRESS) or checking port availability usingtelnet YOUR_VPS_IP_ADDRESS VPN_PORT(for TCP) ornc -uzv YOUR_VPS_IP_ADDRESS VPN_PORT(for UDP). - Client is connected, but there is no internet access:
- DNS problem: Try pinging IP addresses (
ping 8.8.8.8). If IPs ping, but domains don’t, there’s a DNS problem. Check the DNS settings in the VPN server and client configuration. - IP forwarding problem on the server: Make sure
net.ipv4.ip_forward=1(and IPv6, if needed) is set and active. - NAT/MASQUERADE rules problem on the server: Check firewall rules (iptables/nftables, UFW) for address translation. Ensure the correct outgoing network interface is specified.
- Routing problem on the server or client: Check routing tables (
ip route showon Linux). - Low VPN connection speed:
- VPS resource load: Check the CPU, RAM, and network load on the VPS (
top,htop,iftop,nload). The VPS may not be able to handle it. - VPS location: A server location too far from you will lead to high latency and reduced speed.
- OpenVPN protocol: If using OpenVPN over TCP, try UDP – it’s usually faster. Also check the ciphers used – some may be more resource-intensive.
- Problems with the VPS provider: The provider’s channels may be overloaded.
- Your ISP’s limitations: Your ISP may limit the speed for certain types of traffic or ports.
Careful log analysis and step-by-step configuration checks usually help identify and resolve most problems.
Strengthening the Security of Your VPS for VPN
Your VPS for VPN is an entry point to the internet, and it must be as secure as possible. Security consists of several levels.
VPS Security
- Regular updates: Always update the OS and all installed software in a timely manner (
sudo apt update && sudo apt upgrade -y). Set up automatic security updates (e.g., viaunattended-upgrades). - Secure SSH access: Use SSH keys, disable password login and root login. Consider changing the standard SSH port and using Fail2Ban to protect against brute-force SSH and other services.
- Minimize services: Disable and remove all unnecessary services and software from the VPS. The less running, the smaller the attack surface.
- Configured firewall: UFW or iptables/nftables should be configured to allow only necessary ports (SSH, VPN).
- Monitoring and logging: Regularly check system logs (
/var/log/auth.log,/var/log/syslog) for suspicious activity. Consider installing a host-based IDS/IPS (e.g., OSSEC, Wazuh) or security auditing tools (Lynis).
VPN Protocol Security
- OpenVPN:
- Use strong ciphers (e.g., AES-256-GCM) and hashing algorithms (SHA256 or higher).
- Use keys of sufficient length (RSA 2048 bits minimum, preferably 4096; DH parameters of the same length).
- Use
tls-cryptortls-authto protect the control channel. - Regularly update certificates, especially if there is suspicion of compromise. Set up a Certificate Revocation List (CRL).
- WireGuard:
- Uses modern cryptography by default, there is less room for configuration errors.
- Securely store server and client private keys. Do not transmit them over insecure channels.
Your Logging Policy
One of the main reasons for creating your own VPN is log control. By default, OpenVPN and WireGuard may keep some operational logs (connections, errors), but do not log the traffic itself or the websites visited.
- OpenVPN: The level of detail in the logs is configured by the
verbdirective inserver.conf(verb 3is the standard level). Thestatusfile (e.g.,openvpn-status.log) shows current connections. You can configure logging tosyslogor to a separate file (logorlog-appenddirective). - WireGuard: WireGuard itself is very «quiet» and does not keep active traffic logs. Information about recent handshakes and transferred traffic for each peer is visible via
sudo wg show, but it is not persistently stored by default.
Decide for yourself what level of logging you need. For maximum privacy, aim for a minimum of logs related to user activity. Server operational logs for troubleshooting can be helpful.
Legal and Ethical Aspects of Using Your Own VPN
Owning and managing your own VPS for VPN puts a certain responsibility on you:
- Legislation of your country and the country where the VPS is located: Using a VPN is legal in most countries to protect privacy. However, some countries have restrictions or prohibitions. Find out the laws concerning VPNs, both in your country and in the country where your VPS is located.
- Terms of Service/Acceptable Use Policy (ToS/AUP) of the VPS provider: Most providers allow VPNs, but may prohibit certain activities through their network (e.g., spam, DDoS, malware distribution, copyright infringement). Violation of the ToS may lead to your VPS being blocked.
- Responsibility for traffic: You are responsible for all traffic originating from your VPS IP address. If illegal activity is conducted through your VPN, requests from law enforcement (if any) will go to your provider, who in turn may redirect them to you or take action in accordance with their policy.
- Ethical use: Use your VPN responsibly. Not for attacks, spam, or other malicious activity. Remember that while a VPN provides privacy, it does not make you completely anonymous or invulnerable.
Your own VPN is a powerful tool, and like any tool, it can be used for good or for ill. Use it wisely and responsibly.
A Relevant Quote
Arguing that you don’t care about the right to privacy because you have nothing to hide is no different than saying you don’t care about free speech because you have nothing to say.
Edward Snowden
This quote perfectly highlights the importance of privacy in the digital world, and your own VPN server is one step towards ensuring it.
Conclusions: Your Own VPN – Freedom and Control
Colleagues, we have gone through a detailed process of setting up your own VPN server on a VPS. From choosing a suitable VPS for VPN and its initial preparation to deploying the popular OpenVPN and WireGuard VPN on a VPS with Ubuntu. We also touched upon security issues, advanced settings, and troubleshooting. I hope this article has given you all the necessary knowledge and confidence to create your own secure internet tunnel.
What we learned:
- Advantages of your own VPN: Full control, no logs (at your discretion), increased security and privacy, bypassing restrictions, dedicated IP.
- Criteria for choosing a VPS for VPN: Location, KVM virtualization, sufficient resources (RAM, CPU, SSD), good channel, suitable OS (Ubuntu/Debian), provider policy. The process of renting a VPS for VPN has become clearer.
- Initial VPS setup: System updates, creating a sudo user, basic UFW firewall configuration.
- Choosing a VPN protocol: We compared OpenVPN and WireGuard, highlighting WireGuard as preferable for most modern tasks due to its speed and simplicity.
- Step-by-step installation of OpenVPN and WireGuard: We examined both automated methods using scripts (Nyr for OpenVPN, Angristan for WireGuard), and the main steps of manual configuration for a deeper understanding.
- Configuring VPN clients for various platforms.
- Advanced configurations: DNS-leak prevention, Kill Switch, non-standard ports, IPv6, split tunneling.
- Strengthening VPN server security: Protecting the VPS itself and the VPN protocol, managing logs.
- Legal and ethical aspects: Responsible use of VPN.
Creating and using your own VPS for VPN is not only a practical skill that enhances your digital security, but also a step towards greater freedom and control over your data on the internet. This allows you to be independent of the policies of commercial services and be confident in how your traffic is handled. Yes, it requires some effort and technical knowledge, but the result is worth it. Experiment, learn, and stay safe online! Good luck setting up your ideal VPN server!