Overview of the Problem
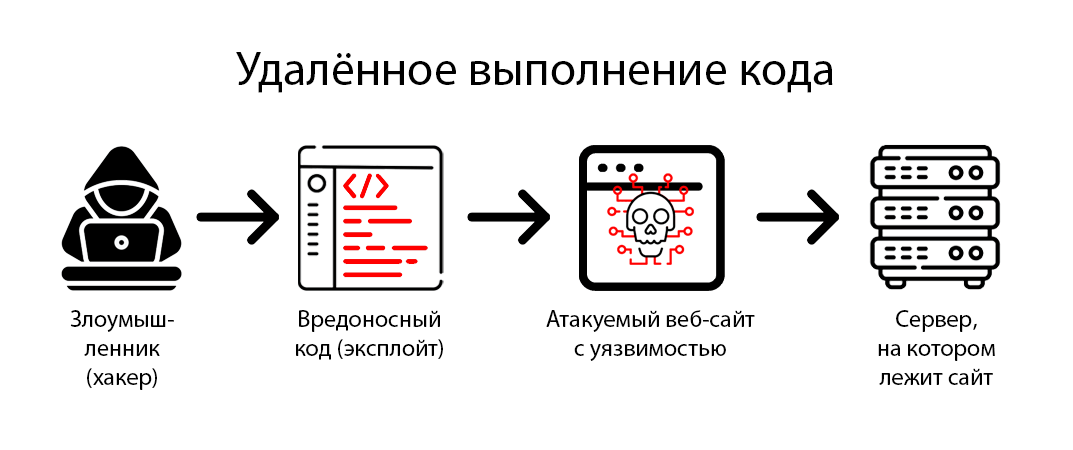
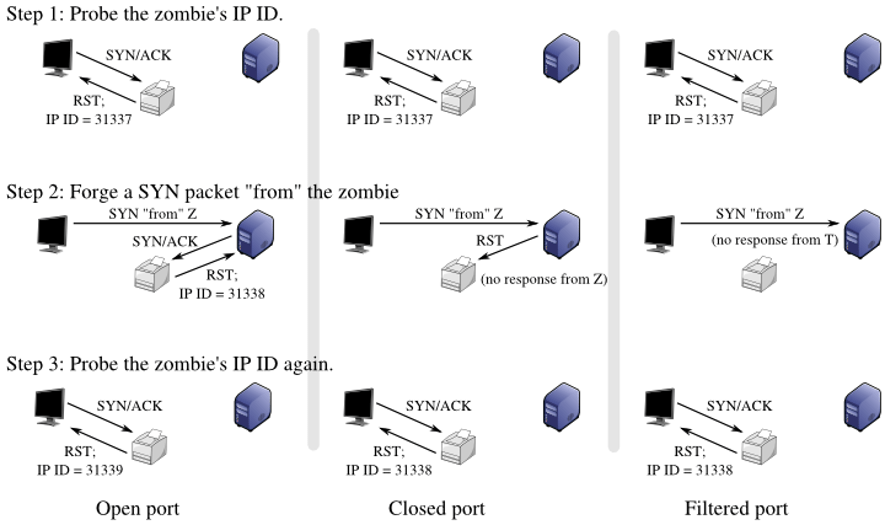
When working with cloud services, server security is a top priority. The ability to access your data from the internet can lead to security threats such as hacking, data leaks, DDoS attacks, and more.
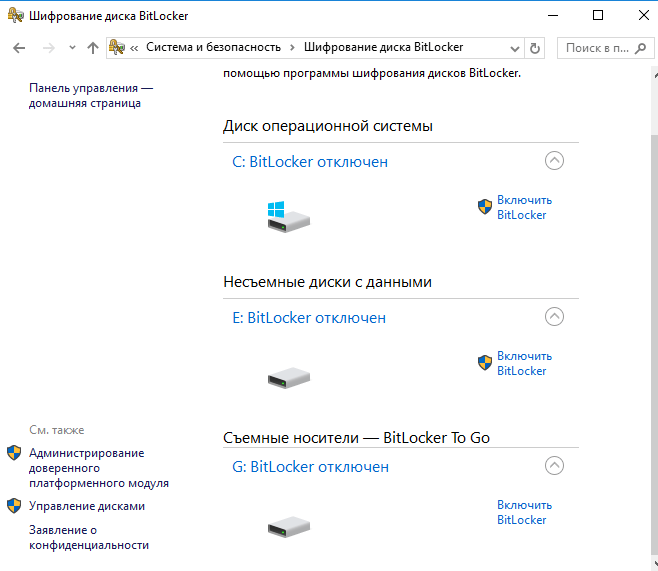
Data Encryption
One of the key methods for ensuring server security when working with cloud services is data encryption. It is important to use strong encryption algorithms to protect sensitive information from unauthorized access. Regularly update encryption keys and keep them stored securely.
Multi-Factor Authentication
To enhance server security, it is recommended to use multi-factor authentication. This method requires the user to provide two or more verifications of their identity to access the system. For example, in addition to a password, you can use an SMS code or biometric data.
Regular Software Updates
It is very important to regularly update the software on the server, including the operating system and application programs. Updates contain vulnerability fixes and new security features that help protect the server from potential threats.
Data Backup
To ensure server security, it is necessary to regularly create data backups. In the event of an emergency or cyberattack, you will be able to recover lost data using backups. It is important to store backups on separate media and in a secure location.
Security Monitoring
To quickly detect security threats, it is recommended to install a monitoring system. This will allow you to track activity on the server, identify anomalous events, and respond to them in real time. If suspicious activity is detected, measures should be taken to block it and prevent damage.
Staff Training
Training staff on information security plays an important role in ensuring server security. Regular training and briefings will help employees understand the basic principles of security, be able to recognize threats and respond to them correctly. It is also important to monitor compliance with security rules and policies in the organization.
Conclusion
Ensuring server security when working with cloud services requires a comprehensive approach and attention to detail. By following the recommendations described above, you can minimize the risks of vulnerabilities and protect your data from unauthorized access.