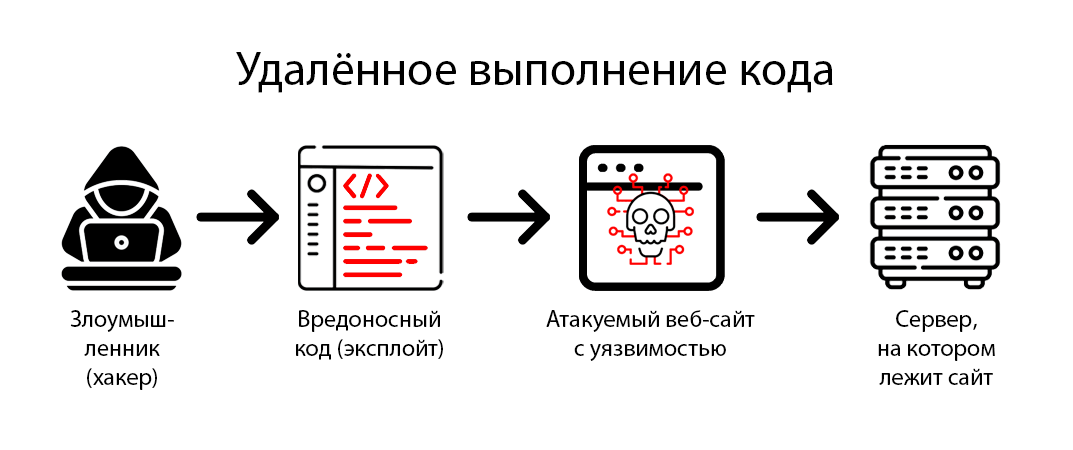
Software Vulnerability Analysis
Before protecting a server from attacks through software vulnerabilities, it’s essential to perform a vulnerability analysis. You can use specialized tools, such as security scanners, which automatically examine the server for potential vulnerabilities.
Software Updates and Patches
One of the primary ways to ensure server security is to update software and install patches. Developers constantly release updates that fix discovered vulnerabilities, so it’s crucial to regularly update all installed software, including the operating system, web server, databases, and other applications.
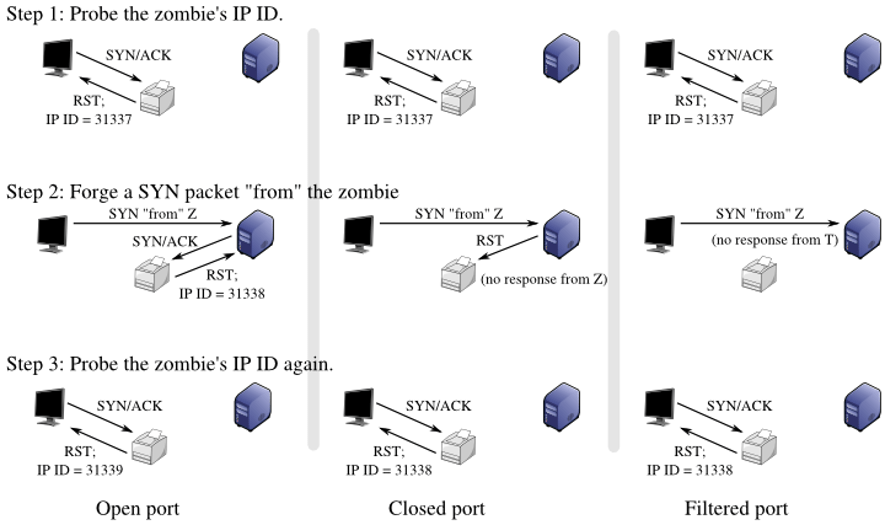
Firewall Configuration
A firewall is the server’s first line of defense against external attacks. It’s necessary to properly configure the firewall to block unauthorized connections and filter malicious traffic. You can configure the firewall to allow access only to specific ports and IP addresses.
Event Monitoring
It’s important to monitor events occurring on the server to respond quickly to potential threats. Event monitoring allows you to track unusual activity, suspicious connections, and other anomalies that may indicate hacking attempts.
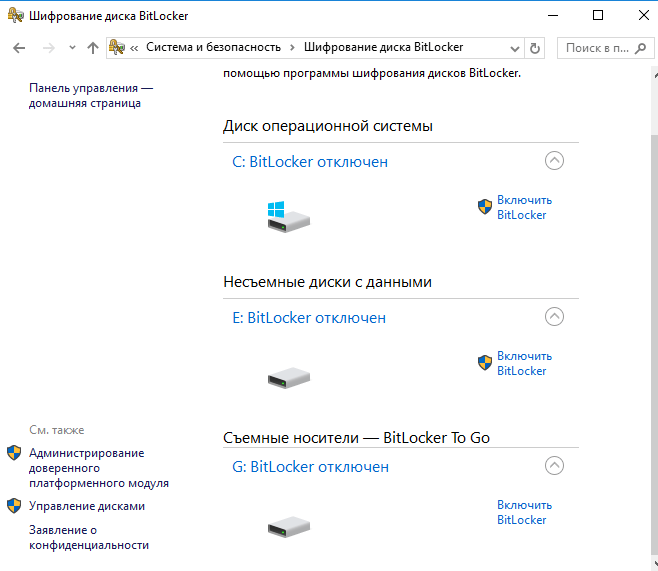
Data Encryption
To protect confidential data on the server, you need to use encryption. Data encryption ensures the confidentiality and integrity of information, preventing the possibility of interception or alteration of data by attackers.
Regular Security Audits
To maintain a high level of server security, it is recommended to conduct regular security audits. An audit will help identify security problems on the server, eliminate vulnerabilities, and improve protection processes.
Data Backup
To ensure reliability and data recovery in the event of an attack or server failure, it is necessary to regularly create data backups. Data backup can help quickly restore server functionality and minimize information loss.
Conclusion
Protecting a server from attacks through software vulnerabilities is an important aspect of ensuring information security. By following the recommendations above and taking security measures, you can protect your server from threats and ensure data integrity.