Threat Analysis
Before discussing methods for protecting a server from internal threats, it is necessary to conduct an analysis of potential threats. Internal threats can be caused by the actions of malicious employees, loss of credentials, insufficient access control, and other factors.
Access Management
One of the key aspects of protecting a server from internal threats is controlling access to resources. It is necessary to determine access levels for employees based on their roles and responsibilities. Regularly update accounts and revoke access as needed. Use the principle of least privilege — grant access only to the necessary resources.
User Activity Monitoring
To detect potential threats, it is necessary to monitor user activity on the server. Use specialized tools to analyze logs and detect anomalous activity. Create processes for responding to suspicious activities and investigating incidents.
Employee Training
Training employees on cybersecurity issues is an important component of protecting against internal threats. Conduct regular training on safe online behavior, inform them about the latest threats and protection methods. Remind them of the importance of adhering to security policies and the mandatory reporting of discovered vulnerabilities.
Software Updates
One of the main ways to protect a server from internal threats is to regularly update software. Install automatic updates for operating systems, applications, and antivirus programs. Update software in a timely manner to close vulnerabilities and reduce the risk of security incidents.
Data Encryption
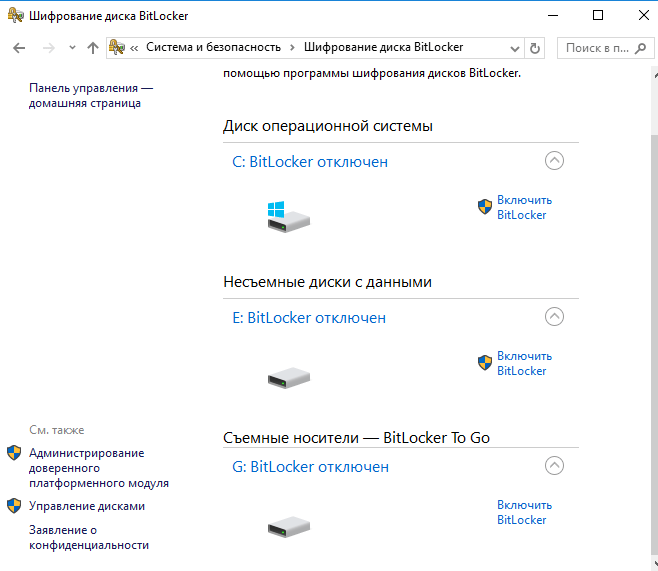
To protect sensitive data on the server, it is recommended to use encryption. Encrypt data at rest and in transit using strong encryption algorithms. Implement an encryption policy at the file system and network connection levels. Regularly audit data encryption and update it in accordance with modern security standards.
Regular Audits and Checks
To ensure effective protection of the server from internal threats, regularly conduct security audits and checks. Analyze vulnerabilities, check compliance with security policies, and conduct data leak checks. Use external specialists to conduct independent security audits and checks.
Final Remarks
Ensuring the protection of a server from internal threats is a complex and multifaceted process that requires constant attention and effort. Use a comprehensive approach to server protection, combining technical measures with employee training and regular security audits. Remember that protection against internal threats is a continuous process, and only constant updating of methods and technologies guarantees effective server protection.