How to Protect Server APIs from Attackers?
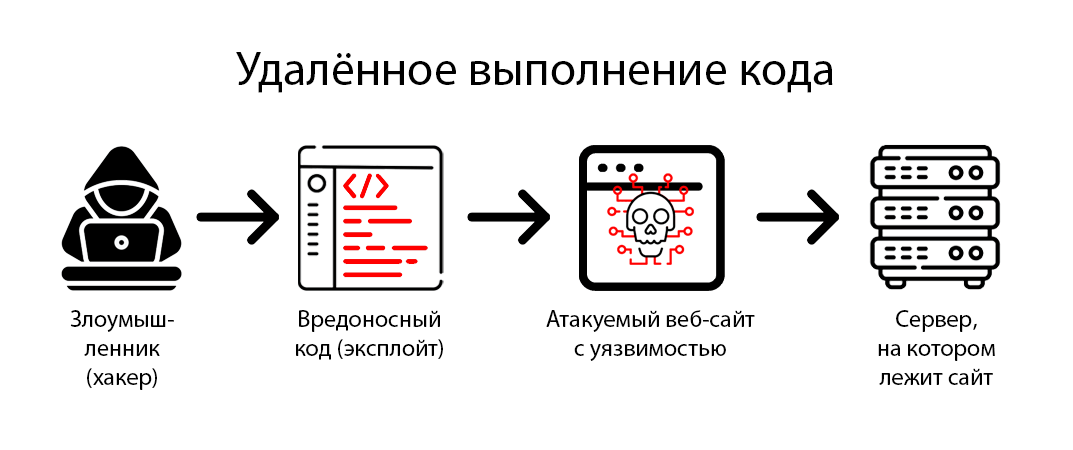
Server APIs are an integral part of modern web applications. However, working with APIs introduces vulnerability to malicious attacks. To protect server APIs from attackers, it is necessary to take a number of measures to ensure data security and confidence in its integrity.
One of the main measures is authentication and authorization. To protect the API from unauthorized access, it is necessary to use authentication mechanisms such as access tokens or API keys. It is also important to properly configure access rights to the API to prevent unauthorized requests.
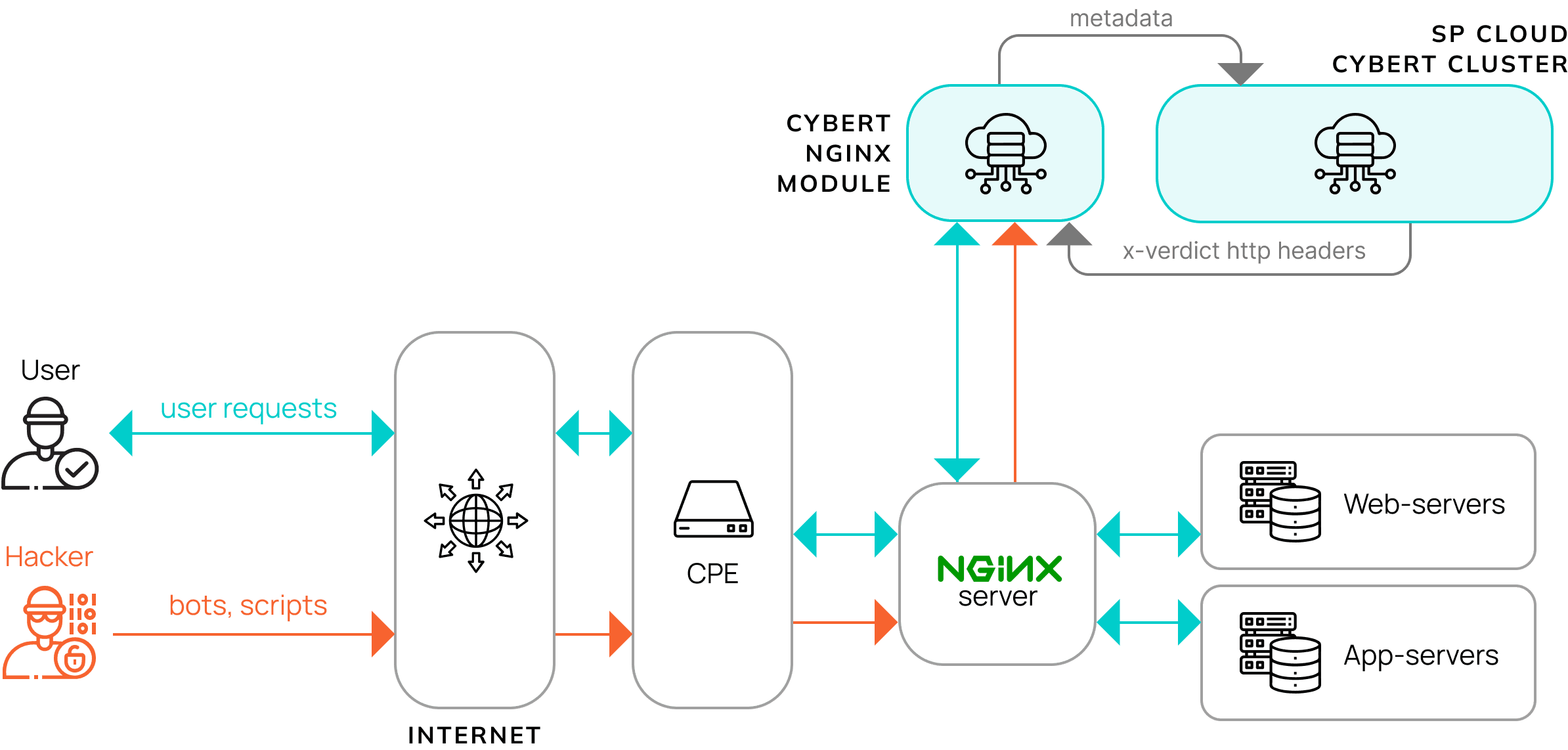
Another way to protect server APIs from attackers is to use the HTTPS protocol for data transmission. HTTPS provides data encryption, making it inaccessible to third parties. It is also important to use additional security measures, such as filtering incoming requests and monitoring server activity.
In addition, to protect server APIs from attackers, it is recommended to regularly update the software and apply security patches. Attackers are constantly looking for vulnerabilities in systems, so it is important to monitor updates and quickly fix discovered vulnerabilities.
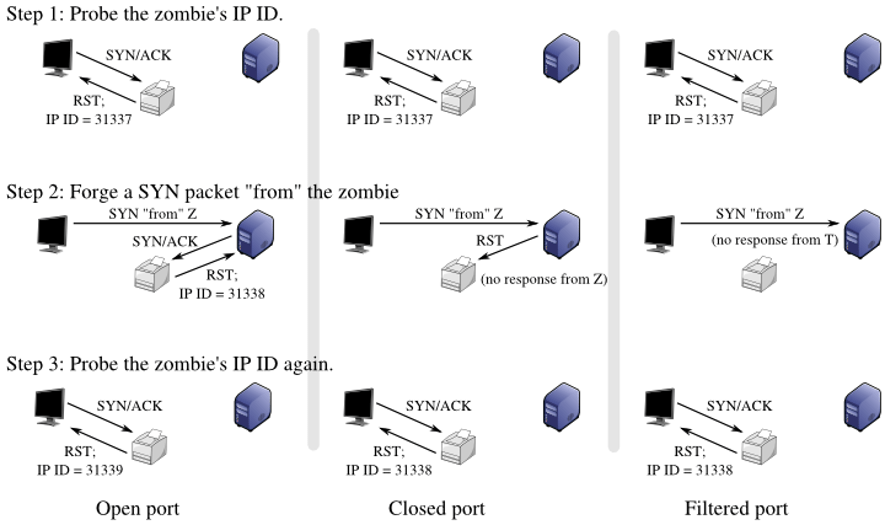
An important aspect of protecting server APIs from attackers is also monitoring network activity. Constant monitoring allows you to quickly identify anomalies and potential attacks, as well as prevent data leaks. Server API security is a continuous process that requires attention and constant monitoring.
In conclusion, protecting server APIs from attackers is an important task for any developer. A properly configured security system will protect data and confidence in its integrity. By following the recommendations for protecting server APIs, you can minimize the likelihood of successful attacks and ensure the security of the web application.