Internet Security [EN]
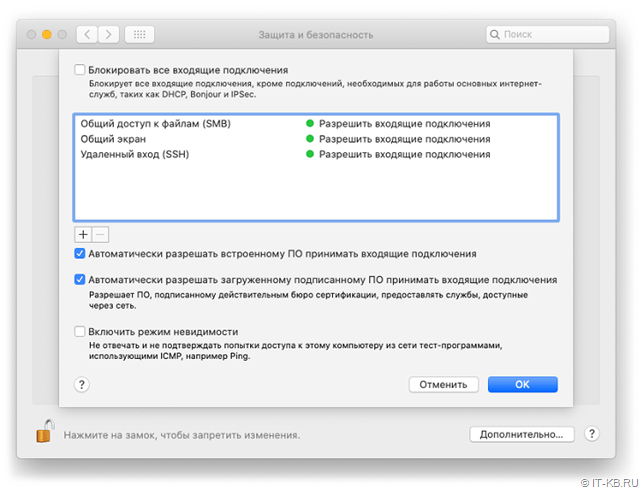
How to Configure the Firewall on Your macOS: A Complete Guide
How to Configure the Firewall in macOS? Every macOS user has the ability to protect their computer with a built-in…
Read More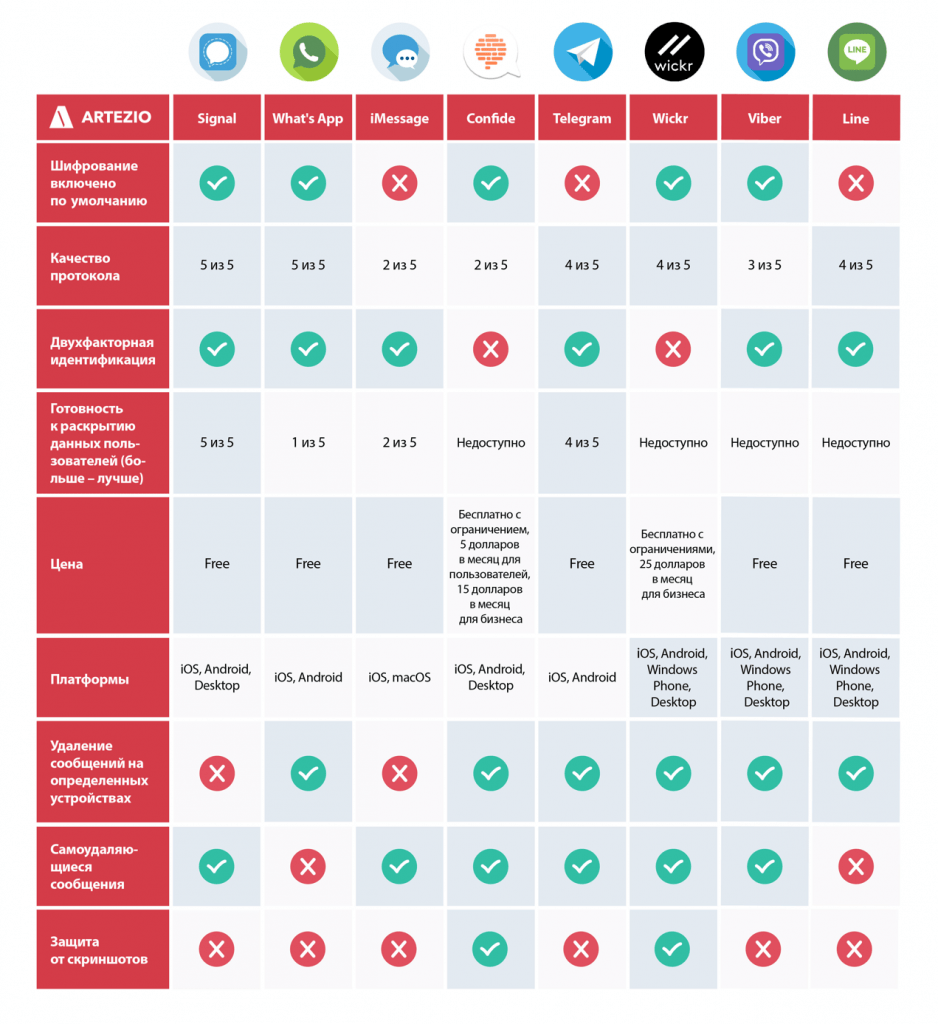
The Most Secure Messaging Apps: A Privacy-Focused Comparison
Which Messengers Are the Most Secure? The modern world demands that we are constantly connected to those around us. Messengers…
Read More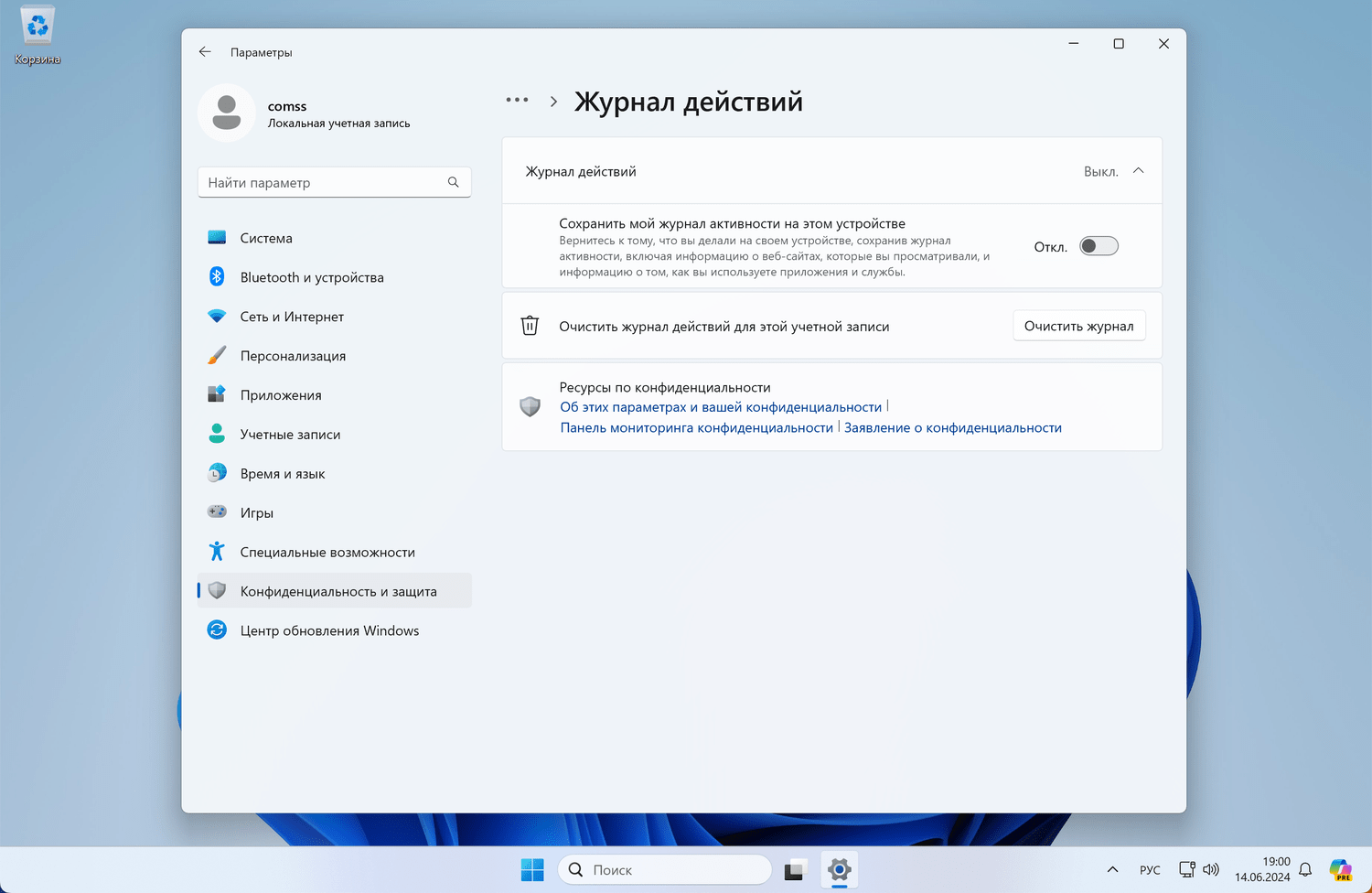
How to Disable Unnecessary Tracking in Windows 11
How to Disable Unnecessary Trackers in Windows 11? One way to protect your privacy in Windows 11 is to disable…
Read More
How to Remove a Keylogger from Your PC: A Complete Guide
How to Remove a Keylogger from Your PC? A keylogger is a program capable of recording all keystrokes on a…
Read More
Check if Your Email Was Hacked: Data Breach Test Guide
How to Check Your Email for Data Breaches? Email is our primary means of communication on the internet. We use…
Read More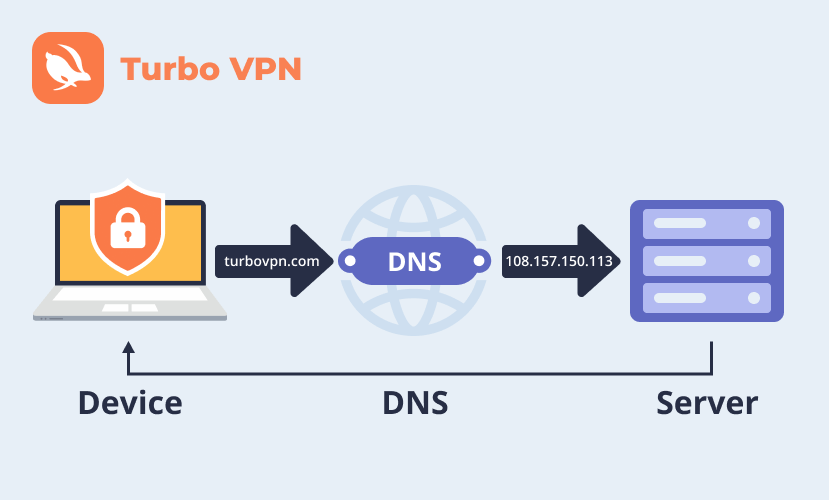
Which DNS Services Offer the Best Protection Against Phishing?
Which DNS Services Protect Against Phishing? Phishing is one of the most common types of online fraud. But even if…
Read More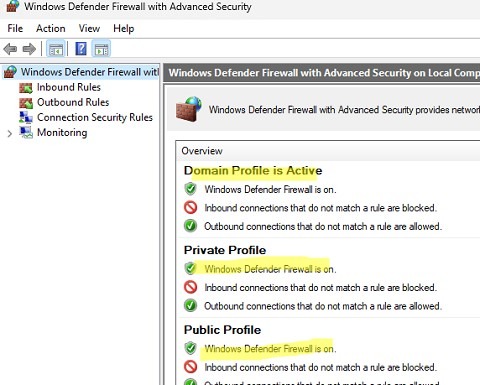
How to Enable Windows Defender Firewall: A Step-by-Step Guide
«`html How to Enable Windows Defender Firewall? Windows Defender Firewall is an important tool to protect your computer from malware…
Read More
What are Signal’s Encrypted Messages and How Do They Work?
What are Encrypted Messages in Signal? Signal is a messenger that provides confidentiality and security for user communications. One of…
Read More
How to Enable Private Browsing Mode in Tor Browser?
How to Enable Anonymity Mode in Tor Browser? The internet is a vast space where millions of users communicate, work,…
Read More
How to Prevent Data Leaks in Telegram: Your Ultimate Privacy Guide
How to Protect Yourself from Data Leaks in Telegram? Telegram is one of the most popular messengers in the world.…
Read MoreSearch
Recent Posts
- How to Test Your VDS Windows Hard Drive Speed? 18.11.2025
- How to Install and Configure Fail2ban on Ubuntu VPS: A Step-by-Step Guide 18.11.2025
- How to Configure Nagios Alerts on a Dedicated Server: A Step-by-Step Guide 17.11.2025
- How to View Running Processes on a Linux Ubuntu VPS in 2025 17.11.2025
- Simple Script to Monitor VDS Disk Space (and Avoid Running Out!) 16.11.2025
Categories
- Backups & Data Recovery [EN] (68)
- Backups & Recovery [EN] (1)
- Backups and Data Recovery [EN] (66)
- Backups and Recovery [EN] (2)
- Data Backup & Recovery [EN] (18)
- Data Backup and Recovery [EN] (19)
- Guides & Instructions [EN] (3)
- Guides and Tutorials [EN] (1)
- Internet Security [EN] (123)
- Performance & Optimization [EN] (30)
- Server Monitoring & Management [EN] (91)
- Server Monitoring and Management [EN] (44)
- Server Security [EN] (129)
- Software & Tools [EN] (93)
- Tech Support & Troubleshooting [EN] (79)
- Technical Support [EN] (79)
- Technical Support & Troubleshooting [EN] (7)
- Troubleshooting [EN] (36)
- VPS & Virtualization [EN] (202)
- VPS and virtualization [EN] (1)
- VPS VDS RDP [EN] (12)
- VPS/VDS/RDP [EN] (99)
- Интернет безопасность [EN] (1)
- Мониторинг и управление сервером [RU] [EN] (54)
- Программное обеспечение и инструменты [EN] (40)
- Техническая поддержка и устранение проблем [EN] (1)
