Internet Security [EN]
**Option 1 (Focus on vulnerability):** Is Your Wi-Fi Network Secure? A Simple Security Check **Option 2 (Focus on assessment):** Wi-Fi Security Assessment: How to Check Your Network’s Vulnerability **Option 3 (Focus on practical guide):** How to Check Wi-Fi Security: A Practical Guide for Home Networks
How to Check the Security of Your Wi-Fi Network? Wi-Fi networks are an integral part of our daily lives. We…
Read More
How to Secure Your TP-Link Router from Hacking: Best Practices
How to Protect Your TP-Link Router from Hacking In our time, network security is an extremely important task. A TP-Link…
Read More
What to Do If Your Password Leaked in a Have I Been Pwned? Database Breach
What to Do If Your Password Leaks into the Have I Been Pwned Database In our time, guaranteeing absolute security…
Read More
How to Configure Windows 10 Firewall: A Step-by-Step Guide
How to Configure the Firewall in Windows 10? The Firewall in Windows 10 is an important program that protects your…
Read More
How to Scan a Website for Viruses with VirusTotal: A Step-by-Step Guide
How to Check a Website for Viruses with VirusTotal? In today’s world, the security of virtual resources plays a huge…
Read More
Best Antivirus for Windows 11: Top Choices & Reviews
What are the Best Antivirus Programs for Windows 11? The Windows 11 operating system is one of the most modern…
Read More
How to Enable Two-Factor Authentication (2FA) in Telegram: A Step-by-Step Guide
How to Enable Two-Factor Authentication in Telegram? Telegram is one of the most popular messengers in the world, providing a…
Read More
Google Authenticator: What It Is and How to Set It Up
What is Google Authenticator and How to Set it Up? Google Authenticator is a mobile app that provides two-factor authentication…
Read More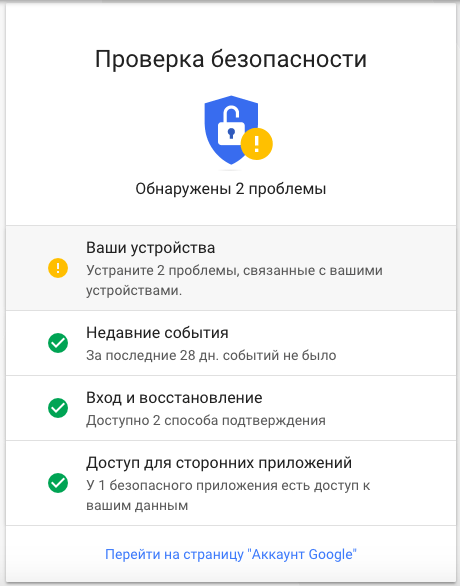
How to Secure Your Google Account: Prevent Hacking and Stay Protected
How to Protect Your Google Account from Hacking? Internet security is becoming an increasingly relevant topic, as many of us…
Read More
Detecting Unauthorized Port Scanning in Real-Time
How to Detect Unauthorized Port Scanning in Real Time Introduction Unauthorized port scanning is one of the most common attacks…
Read MoreSearch
Recent Posts
- How to Test Your VDS Windows Hard Drive Speed? 18.11.2025
- How to Install and Configure Fail2ban on Ubuntu VPS: A Step-by-Step Guide 18.11.2025
- How to Configure Nagios Alerts on a Dedicated Server: A Step-by-Step Guide 17.11.2025
- How to View Running Processes on a Linux Ubuntu VPS in 2025 17.11.2025
- Simple Script to Monitor VDS Disk Space (and Avoid Running Out!) 16.11.2025
Categories
- Backups & Data Recovery [EN] (68)
- Backups & Recovery [EN] (1)
- Backups and Data Recovery [EN] (66)
- Backups and Recovery [EN] (2)
- Data Backup & Recovery [EN] (18)
- Data Backup and Recovery [EN] (19)
- Guides & Instructions [EN] (3)
- Guides and Tutorials [EN] (1)
- Internet Security [EN] (123)
- Performance & Optimization [EN] (30)
- Server Monitoring & Management [EN] (91)
- Server Monitoring and Management [EN] (44)
- Server Security [EN] (129)
- Software & Tools [EN] (93)
- Tech Support & Troubleshooting [EN] (79)
- Technical Support [EN] (79)
- Technical Support & Troubleshooting [EN] (7)
- Troubleshooting [EN] (36)
- VPS & Virtualization [EN] (202)
- VPS and virtualization [EN] (1)
- VPS VDS RDP [EN] (12)
- VPS/VDS/RDP [EN] (99)
- Интернет безопасность [EN] (1)
- Мониторинг и управление сервером [RU] [EN] (54)
- Программное обеспечение и инструменты [EN] (40)
- Техническая поддержка и устранение проблем [EN] (1)
