Internet Security [EN]

Configure OpenDNS for Enhanced Internet Security: A Step-by-Step Guide
How to Configure OpenDNS for Internet Protection? OpenDNS is a convenient and effective way to protect your internet connection from…
Read More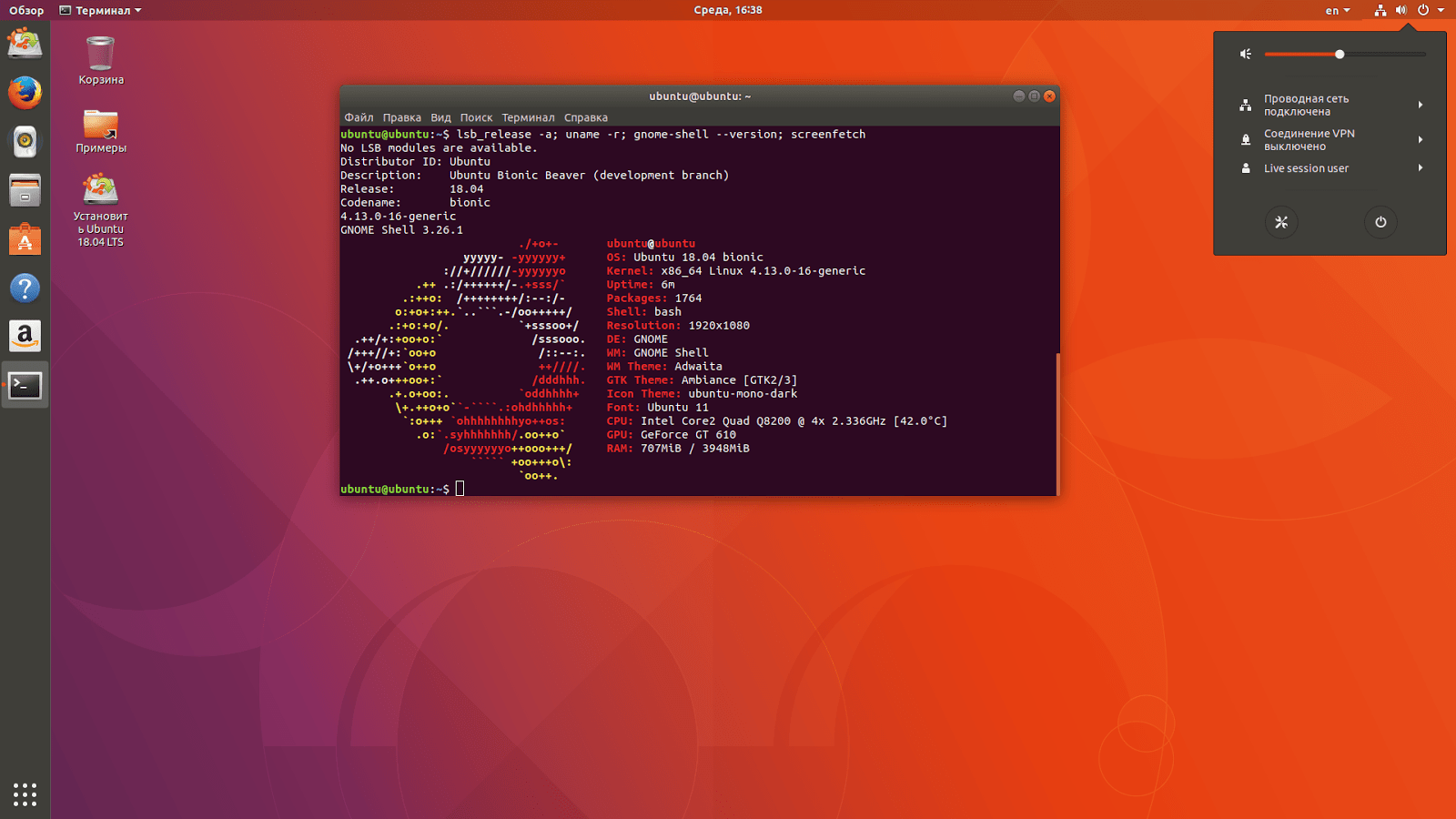
How to Configure the UFW Firewall on Ubuntu: A Step-by-Step Guide
How to Configure the UFW Firewall in Ubuntu? UFW, or Uncomplicated Firewall, is an easy-to-use tool for managing the firewall…
Read More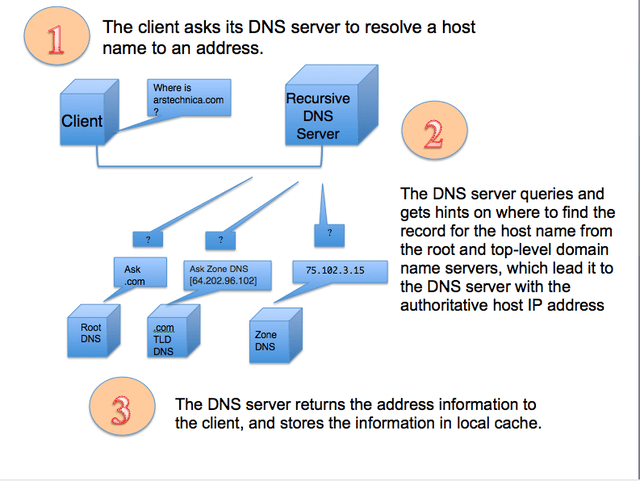
DNS Servers That Don’t Log: Which to Choose?
Which DNS Services Don’t Keep Logs? DNS servers play an important role on the Internet, providing the translation of domain…
Read More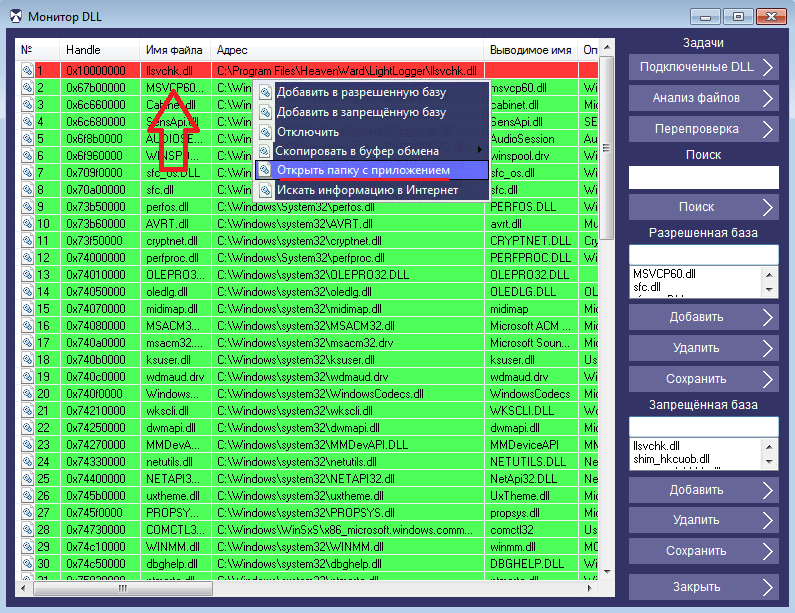
How to Remove a Keylogger from Your PC: A Complete Guide
How to Remove a Keylogger from Your PC? A keylogger is a program capable of recording all keystrokes on a…
Read More
How to Block IPs with Cloudflare: A Step-by-Step Guide
How to Configure IP Blocking via Cloudflare? Cloudflare is a popular service that helps protect your site from DDoS attacks,…
Read More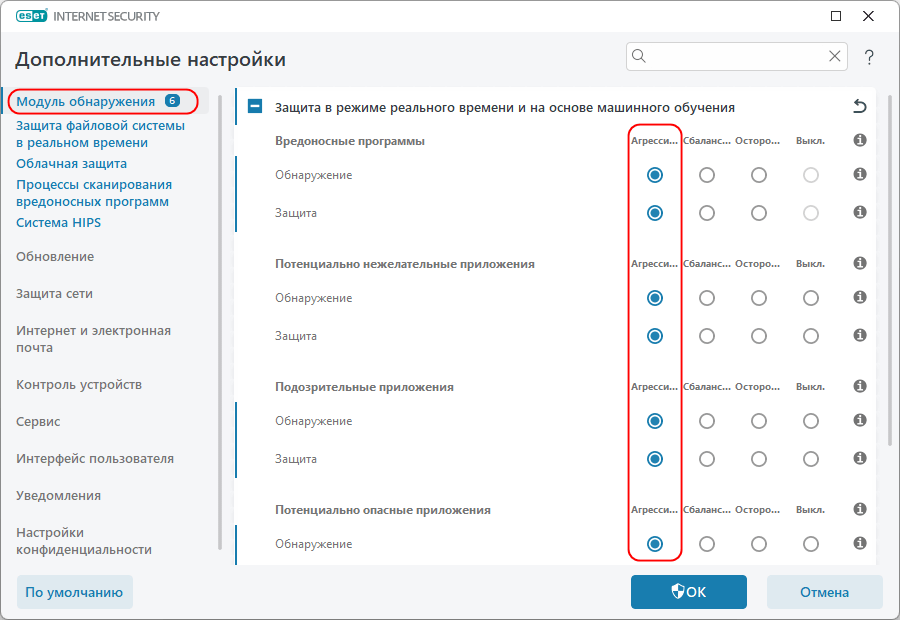
**Option 1 (Shorter):** * ESET NOD32: Maximize Your Protection with These Settings **Option 2 (More Specific):** * ESET NOD32 Configuration: Best Settings for Maximum Security **Option 3 (Question format):** * How to Configure ESET NOD32 for Ultimate Protection?
«`html How to Configure ESET NOD32 for Maximum Protection? How to Configure ESET NOD32 for Maximum Protection? Purchasing antivirus software…
Read More
How to Set Up OpenVPN for a Secure Connection: A Complete Guide
How to Set Up OpenVPN for a Secure Connection? OpenVPN is one of the most popular and reliable solutions for…
Read More
**Option 1 (Focus on vulnerability):** Is Your Wi-Fi Network Secure? A Simple Security Check **Option 2 (Focus on assessment):** Wi-Fi Security Assessment: How to Check Your Network’s Vulnerability **Option 3 (Focus on practical guide):** How to Check Wi-Fi Security: A Practical Guide for Home Networks
How to Check the Security of Your Wi-Fi Network? Wi-Fi networks are an integral part of our daily lives. We…
Read More
Detecting Unauthorized Port Scanning in Real-Time
How to Detect Unauthorized Port Scanning in Real Time Introduction Unauthorized port scanning is one of the most common attacks…
Read More
How to Protect Your Network Devices from Port Scanning
How to Protect Network Devices from Port Scanning Introduction Understanding the importance of protecting network devices from port scanning is…
Read MoreSearch
Recent Posts
- How to Test Your VDS Windows Hard Drive Speed? 18.11.2025
- How to Install and Configure Fail2ban on Ubuntu VPS: A Step-by-Step Guide 18.11.2025
- How to Configure Nagios Alerts on a Dedicated Server: A Step-by-Step Guide 17.11.2025
- How to View Running Processes on a Linux Ubuntu VPS in 2025 17.11.2025
- Simple Script to Monitor VDS Disk Space (and Avoid Running Out!) 16.11.2025
Categories
- Backups & Data Recovery [EN] (64)
- Backups & Recovery [EN] (1)
- Backups and Data Recovery [EN] (65)
- Backups and Recovery [EN] (2)
- Data Backup & Recovery [EN] (18)
- Data Backup and Recovery [EN] (19)
- Guides and Tutorials [EN] (1)
- Internet Security [EN] (12)
- Performance & Optimization [EN] (30)
- Server Monitoring & Management [EN] (91)
- Server Monitoring and Management [EN] (44)
- Server Security [EN] (129)
- Software & Tools [EN] (13)
- Tech Support & Troubleshooting [EN] (79)
- Technical Support [EN] (79)
- Technical Support & Troubleshooting [EN] (7)
- Troubleshooting [EN] (36)
- VPS & Virtualization [EN] (201)
- VPS and virtualization [EN] (1)
- VPS VDS RDP [EN] (12)
- VPS/VDS/RDP [EN] (93)
- Мониторинг и управление сервером [RU] [EN] (54)
- Техническая поддержка и устранение проблем [EN] (1)
